Scenario: Use certificates for internal authentication
In this scenario, you to learn how to use certificates as an authentication mechanism to protect and restrict which resources and applications that internal users can access on your internal servers.
Situation
You are the network administrator for a company (MyCo, Inc.) whose human resource department is concerned with such issues as legal matters and privacy of records. Company employees have requested that they be able to access their personal benefits and health care information online. The company has responded to this request by creating an internal Web site to provide this information to employees. You are responsible for administering this internal Web site, which runs on the IBM® HTTP Server for i5/OS™ (powered by Apache).
Because employees are located in two geographically separate offices and some employees travel frequently, you are concerned about keeping this information private as it travels across the Internet. Also, you traditionally authenticate users by means of a user name and password to limit access to company data. Because of the sensitive and private nature of this data, you realize that limiting access to it based on password authentication may not be sufficient. After all, people can share, forget, and even steal passwords.
After some research, you decide that using digital certificates can provide you with the security that you need. Using certificates allows you to use Secure Sockets Layer (SSL) to protect the transmission of the data. Additionally, you can use certificates instead of passwords to more securely authenticate users and limit the human resource information that they can access.
Therefore, you decide to set up a private Local Certificate Authority (CA) and issue certificates to all employees and have the employees associate their certificates with their iSeries™ user profiles. This type of private certificate implementation allows you to more tightly control access to sensitive data, as well as control the privacy of the data by using SSL. Ultimately, by issuing certificates yourself, you have increased the probability that your data remains secure and is accessible only to specific individuals.
Scenario advantages
This scenario has the following advantages:
- Using digital certificates to configure SSL access to your human resource Web server ensures that the information transmitted between the server and client is protected and private.
- Using digital certificates for client authentication provides a more secure method of identifying authorized users.
- Using private digital certificates to authenticate users to your
applications and data is a practical choice under these or similar conditions:
- You require a high degree of security, especially in regards to authenticating users.
- You trust the individuals to whom you issue certificates.
- Your users already have iSeries user profiles for controlling their access to applications and data.
- You want to operate your own Certificate Authority (CA).
- Using private certificates for client authentication allows you to more easily associate the certificate with the authorized user's iSeries user profile. This association of certificate with a user profile allows the HTTP Server to determine the certificate owner's user profile during authentication. The HTTP Server can then swap to it and run under that user profile or perform actions for that user based on information in the user profile.
Objectives
In this scenario, MyCo, Inc. wants to use digital certificates to protect the sensitive personal information that their internal human resources Web site provides to company employees. The company also wants a more secure method of authenticating those users who are allowed to access this Web site.
- Company internal human resources Web site must use SSL to protect the privacy of the data that it provides to users.
- SSL configuration must be accomplished with private certificates from an internal Local Certificate Authority (CA).
- Authorized users must provide a valid certificate to access the human resources Web site in SSL mode.
Details
The following figure illustrates the network configuration for this scenario:
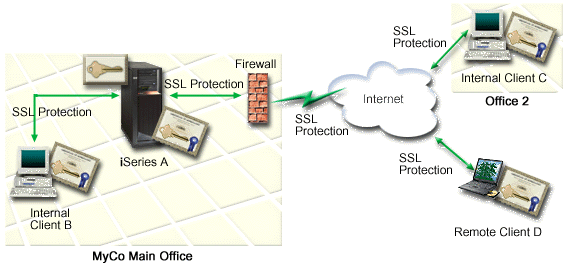
The figure illustrates the following information about the situation for this scenario:
- iSeries A is the server that hosts the company's rate calculating application.
- iSeries A runs i5/OS Version 5 Release 4 (V5R4).
- iSeries A has Digital Certificate Manager (i5/OS option 34) and IBM HTTP Server for i5/OS (5722–DG1) installed and configured.
- iSeries A runs the rate
calculating application, which is configured such that it:
- Requires SSL mode.
- Uses a public certificate from a well-known Certificate Authority (CA) to authenticate itself to initialize an SSL session.
- Requires user authentication by user name and password.
- iSeries A presents its certificate to initiate an SSL session when Clients B and C access the rate calculating application.
- After initializing the SSL session, iSeries A requests that Clients B and C provide a valid user name and password before allowing access to the rate calculating application.
- Clients B and C are independent agents who access the rate calculating application.
- Clients B and C client software has an installed copy of the well-known CA certificate that issued the application certificate.
- Clients B and C access the rate calculating application on iSeries A, which presents its certificate to their client software to authenticate its identity and initiate an SSL session.
- Client software on Clients B and C is configured to accept the certificate fromiSeries A for the purpose of initializing an SSL session.
- After the SSL session begins, Clients B and C must provide a valid user name and password before iSeries A grants access to the application.
Prerequisites and assumptions
This scenario depends on the following prerequisites and assumptions:
- TheIBM HTTP Server for i5/OS (powered by Apache) runs the human resource application on iSeries A. This scenario does not provide specific instructions for configuring the HTTP Server to use SSL. This scenario provides instructions for configuring and managing the certificates that are necessary for any application to use SSL.
- The HTTP Server provides the capability of requiring certificates for client authentication. This scenario provides instructions for using Digital Certificate Manager (DCM) to configure the certificate management requirements for this scenario. However, this scenario does not provide the specific configuration steps for configuring certificate client authentication for the HTTP Server.
- The human resources HTTP Server on iSeries A already uses password authentication.
- iSeries A meets the requirements for installing and using Digital Certificate Manager (DCM).
- No one has previously configured or used DCM on iSeries A.
- Whoever uses DCM to perform the tasks in this scenario must have *SECADM and *ALLOBJ special authorities for their user profile.
- iSeries A does not have an IBM Cryptographic Coprocessor installed.
Configuration tasks
- Complete planning work sheets
- Configure the human resources HTTP Server to use SSL
- Create and operate a Local CA
- Configure client authentication for human resources Web server
- Start the human resources Web server in SSL mode
- Have users install a copy of the Local CA certificate in their browser
- Have each user request a certificate from the Local CA