Use the following scenario to become familiar with the prerequisites and objectives for using Kerberos authentication between Management Central servers.
Situation
You are a network administrator for a medium-sized parts manufacturer. You currently manage four iSeries™ systems using iSeries Navigator on a client PC. You want your Management Central server jobs to use Kerberos authentication instead of other authentication methods you have used in the past, namely password synchronization.
Objectives
In this scenario, the goal for MyCo, Inc. is to use Kerberos authentication among Management Central servers.
Details
The following graphic shows the details for this scenario.
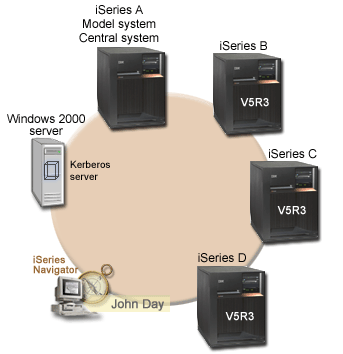
 Runs i5/OS™ Version 5 Release 3 (V5R3) or later with the
following options and licensed products installed:
Runs i5/OS™ Version 5 Release 3 (V5R3) or later with the
following options and licensed products installed:
- i5/OS Host Servers (5722-SS1 Option 12)
- iSeries Access for Windows® (5722-XE1)
 Network Authentication Enablement (5722-NAE) if you are using
V5R4 or later
Network Authentication Enablement (5722-NAE) if you are using
V5R4 or later
 Cryptographic Access Provider (5722-AC3) if you are running
V5R3
Cryptographic Access Provider (5722-AC3) if you are running
V5R3
- i5/OS service principal, krbsvr400/iseriesa.myco.com@MYCO.COM, and associated password have been added to the keytab file.
- Stores, schedules and runs synchronize setting tasks for each of the endpoint systems.
 Runs i5/OS Version 5 Release 3 (V5R3) or later with the
following options and licensed products installed:
Runs i5/OS Version 5 Release 3 (V5R3) or later with the
following options and licensed products installed:- i5/OS Host Servers (5722-SS1 Option 12)
- iSeries Access for Windows (5722-XE1)
- Network Authentication Enablement (5722-NAE) if you are using V5R4 or later
- Cryptographic Access Provider (5722-AC3) if you are running V5R3

- i5/OS service principal, krbsvr400/iseriesb.myco.com@MYCO.COM, and associated password have been added to the keytab file.
 Runs i5/OS Version 5 Release 4 (V5R4) with the following
options and licensed products installed:
Runs i5/OS Version 5 Release 4 (V5R4) with the following
options and licensed products installed:
- i5/OS Host Servers (5722-SS1 Option 12)
- iSeries Access for Windows (5722-XE1)
 Network Authentication Enablement (5722-NAE)
Network Authentication Enablement (5722-NAE)
- i5/OS service principal, krbsvr400/iseriesc.myco.com@MYCO.COM, and associated password have been added to the keytab file.
 Runs i5/OS Version 5 Release 3 (V5R3) or later with the
following options and licensed products installed:
Runs i5/OS Version 5 Release 3 (V5R3) or later with the
following options and licensed products installed:
- i5/OS Host Servers (5722-SS1 Option 12)
- iSeries Access for Windows (5722-XE1)
 Cryptographic Access Provider (5722-AC3)
Cryptographic Access Provider (5722-AC3)
- i5/OS service principal, krbsvr400/iseriesd.myco.com@MYCO.COM, and associated password have been added to the keytab file.
- Operates as the Kerberos server for these systems.
- The following i5/OS service principals have been added to the Windows 2000
server:
- krbsvr400/iseriesa.myco.com@MYCO.COM
- krbsvr400/iseriesb.myco.com@MYCO.COM
- krbsvr400/iseriesc.myco.com@MYCO.COM
- krbsvr400/iseriesd.myco.com@MYCO.COM
Client PC
- Runs iSeries Access for Windows (5722-XE1).
- Runs iSeries Navigator
with the following subcomponents:Note: Only required for PC used to administer network authentication service.
- Network
- Security
 The KDC server name, kdc1.myco.com, and the
hostname, iseriesa.myco.com are fictitious names used in this scenario.
The KDC server name, kdc1.myco.com, and the
hostname, iseriesa.myco.com are fictitious names used in this scenario.
Prerequisites and assumptions
- All system requirements, including software and operating system installation,
have been verified.To verify that the licensed programs have been installed, complete the following:
- In iSeries Navigator, expand .
- Ensure that all the necessary licensed programs are installed.
- All necessary hardware planning and setup have been completed.
- TCP/IP and basic system security have been configured and tested on each of these servers.
- No one has changed the default settings in iSeries Navigator to stop the Task Status
window from opening when a task starts. To verify that the default setting
has not been changed, follow these steps:
- In iSeries Navigator, right-click and select User Preferences.
- On the General page, verify that Automatically open a task status window when one of my tasks starts is selected.
- This scenario is based on the assumption that network authentication service has been configured on each system using the Synchronize Functions wizard in iSeries Navigator. This wizard propagates network authentication service configuration from a model system to multiple target systems. See Scenario: Propagate network authentication service configuration across multiple systems for details on how to use the Synchronize Functions wizard.
Configuration steps
To configure Kerberos authentication between Management Central servers, perform these steps.