Use the following scenario to become familiar with the prerequisites and objectives for propagating your network authentication service configuration across multiple systems.
Situation
You are a systems administrator for a large auto parts manufacturer. You currently manage five iSeries™ systems with iSeries Navigator. One system operates as the central system, which stores data and manages these other systems. The security administrator for your company has just configured network authentication service on a new system to participate in a Windows® 2000 domain, which authenticates users to the enterprise. The security administrator has tested the network authentication service configuration on this system and has successfully obtained a service ticket for this iSeries server. You want to simplify the configuration of network authentication service among these systems that you manage.
Using the Synchronize Functions wizard, you want to take the network authentication service configuration on the model system and apply it to your other systems. The Synchronize Functions wizard will make network authentication service configuration throughout your network quicker and easier since you will not need to configure each system separately.
Because one of the systems runs i5/OS™ Version 5 Release 2 (V5R2) and this release does not support the Synchronize Functions wizard, you will need to configure your V5R2 system using the network authentication service wizard. You will need to configure this system to match the current network authentication service configuration on your model system.
Objectives
- To simplify configuration of network authentication service in the network.
- To have all iSeries systems point to the same Kerberos server.
- To configure a V5R2 system to also participate in the Kerberos realm.
Details
The following graphic shows the details for this scenario.
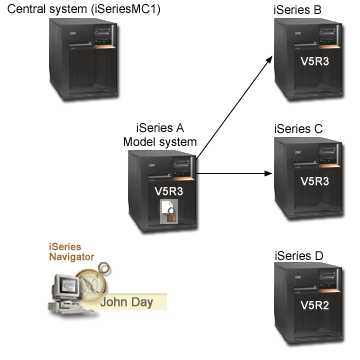
 Runs i5/OS Version 5 Release 3 (V5R3) or later with the
following options and licensed products installed:
Runs i5/OS Version 5 Release 3 (V5R3) or later with the
following options and licensed products installed:
- i5/OS Host Servers (5722-SS1 Option 12)
- iSeries Access for Windows (5722-XE1)
 Network Authentication Enablement (5722-NAE) if you are using
V5R4 or later
Network Authentication Enablement (5722-NAE) if you are using
V5R4 or later
 Cryptographic Access Provider (5722-AC3) if you are running
V5R3
Cryptographic Access Provider (5722-AC3) if you are running
V5R3
- Stores, schedules and runs synchronize setting tasks for each of the endpoint systems.
 Runs i5/OS Version 5 Release 3 (V5R3) or later with the
following options and licensed products installed:
Runs i5/OS Version 5 Release 3 (V5R3) or later with the
following options and licensed products installed:
- i5/OS Host Servers (5722-SS1 Option 12)
- iSeries Access for Windows (5722-XE1)
 Network Authentication Enablement (5722-NAE) if you are using
V5R4 or later
Network Authentication Enablement (5722-NAE) if you are using
V5R4 or later
 Cryptographic Access Provider (5722-AC3) if you are running
V5R3
Cryptographic Access Provider (5722-AC3) if you are running
V5R3
- Is the model system for propagating network authentication service configuration to endpoint systems.
 Runs i5/OS Version 5 Release 3 (V5R3) or later with the
following options and licensed products installed:
Runs i5/OS Version 5 Release 3 (V5R3) or later with the
following options and licensed products installed:
- i5/OS Host Servers (5722-SS1 Option 12)
- iSeries Access for Windows (5722-XE1)
 Network Authentication Enablement (5722-NAE) if you are using
V5R4 or later
Network Authentication Enablement (5722-NAE) if you are using
V5R4 or later
 Cryptographic Access Provider (5722-AC3) if you are running
V5R3
Cryptographic Access Provider (5722-AC3) if you are running
V5R3
- Is one of the endpoint systems for the propagation of network authentication service configuration.
- Runs i5/OS Version
5 Release 3 (V5R3) with the following options and licensed products installed:
- i5/OS Host Servers (5722-SS1 Option 12)
- iSeries Access for Windows (5722-XE1)
 Cryptographic Access Provider (5722-AC3)
Cryptographic Access Provider (5722-AC3)
- Is one of the endpoint systems for the propagation of network authentication service configuration.
- Runs i5/OS Version
5 Release 2 (V5R2) with the following options and licensed products installed:
- i5/OS Host Servers (5722-SS1 Option 12)
- iSeries Access for Windows (5722-XE1)
- Cryptographic Access Provider (5722-AC3)
- Has the following V5R2 PTFs (program temporary fixes) applied:
- SI08977
- SI08979
- Requires separate configuration of network authentication service using the Network Authentication Service wizard in iSeries Navigator.
- Runs iSeries Access for Windows (5722-XE1).
- Runs iSeries Navigator
with the following subcomponents:Note: Only required for PC used to administer network authentication service.
- Network
- Security
Windows 2000 server (not shown in graphic)
- Operates as the Kerberos server for the network (kdc1.myco.com).
- All users have been added to Microsoft® Windows Active Directory.
 The KDC server name, kdc1.myco.com, is a fictitious
name used in this scenario.
The KDC server name, kdc1.myco.com, is a fictitious
name used in this scenario.
Prerequisites and assumptions
- All system requirements, including software and operating system installation,
have been verified.To verify that these licensed programs have been installed, complete the following:
- In iSeries Navigator, expand .
- Ensure that all the necessary licensed programs are installed.
- All necessary hardware planning and setup have been completed.
- TCP/IP and basic system security have been configured and tested on iSeries A.
- No one has changed the default settings in iSeries Navigator to disable the Task
Status window from opening when a task starts. To verify that the default
setting has not been changed, follow these steps:
- In iSeries Navigator, right-click and select User Preferences.
- On the General page, verify that Automatically open a task status window when one of my tasks starts is selected.
- Secure Sockets Layer (SSL) has been configured to protect the transmission
of data between these servers. Note: When you propagate network configuration service configuration among servers, sensitive information like passwords are sent across the network. You should use SSL to protect this information, especially if it is being sent outside your Local Area Network (LAN). See Scenario: Secure all connections to your Management Central server with SSL for details.
- This scenario assumes that Network authentication service is properly configured on the model system (iSeries A).
- All system requirements, including software and operating system installation,
have been verified.To verify that these licensed programs have been installed, complete the following:
- In iSeries Navigator, expand .
- Ensure that all the necessary licensed programs are installed.
- All necessary hardware planning and setup have been completed.
- TCP/IP and basic system security have been configured and tested on your iSeries server.
- Secure Sockets Layer (SSL) has been configured to protect the transmission
of data between these servers. Note: When you propagate network configuration service configuration among servers, sensitive information like passwords are sent across the network. You should use SSL to protect this information, especially if it is being sent outside your Local Area Network (LAN). See Scenario: Secure all connections to your Management Central server with SSL for details.
- All system requirements, including software and operating system installation,
have been verified.To verify that these licensed programs have been installed, complete the following:
- In iSeries Navigator, expand .
- Ensure that all the necessary licensed programs are installed.
- All necessary hardware planning and setup have been completed.
- TCP/IP and basic system security have been configured and tested on your iSeries server.
- Secure Sockets Layer (SSL) has been configured to protect the transmission
of data between these servers. Note: When you propagate network configuration service configuration among servers, sensitive information like passwords are sent across the network. You should use SSL to protect this information, especially if it is being sent outside your Local Area Network (LAN). See Scenario: Secure all connections to your Management Central server with SSL for details.
- All necessary hardware planning and setup have been completed.
- TCP/IP has been configured and tested on the server.
- Windows domain has been configured and tested.
- All users within your network have been added to a Windows domain through Active Directory.