Use the following scenario to become familiar with the prerequisites and objectives of adding network authentication service to your network.
Situation
You are a network administrator that manages the network for the order receiving department in your company. You recently added an iSeries™ to your network to house several necessary applications for your department. In your network you manage users with Microsoft® Windows® Active Directory on a Microsoft Windows 2000 server. Currently all of your users have workstations that run Microsoft Windows 2000 operating system. You have your own Kerberos-enabled applications that use Generic Security Services (GSS) APIs.
This scenario has the following advantages:
- Simplifies authentication process for users
- Eases the overhead of managing access to servers in the network
- Minimizes threat of password theft
Objectives
In this scenario, MyCo, Inc. wants to add an iSeries system to an existing realm where a Windows 2000 server acts as the Kerberos server. The iSeries contains several business critical applications that need to be accessed by the correct users. Users need to be authenticated by the Kerberos server to gain access to these applications.
The objectives of this scenario are as follows:
- To allow the iSeries to participate with an existing Kerberos server
- To allow for both principal names and user names in the network
- To allow Kerberos users to change their own passwords on the Kerberos server
Details
The following figure illustrates the network characteristics of MyCo.
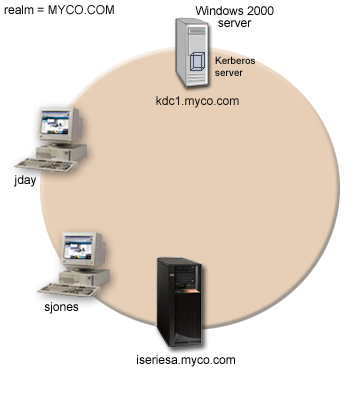
iSeries A
 Runs i5/OS™ Version 5 Release 3 (V5R3) or later with the
following options and licensed products installed:
Runs i5/OS™ Version 5 Release 3 (V5R3) or later with the
following options and licensed products installed:
- i5/OS Host Servers (5722-SS1 Option 12)
- Qshell Interpreter (5722-SS1 Option 30)
- iSeries Access for Windows (5722-XE1)
 Network Authentication Enablement (5722-NAE) if you are using
V5R4 or later
Network Authentication Enablement (5722-NAE) if you are using
V5R4 or later
 Cryptographic Access Provider (5722-AC3) if you are running
V5R3
Cryptographic Access Provider (5722-AC3) if you are running
V5R3
- iSeries A's principal name is krbsvr400/iseriesa.myco.com@MYCO.COM
Windows 2000 server
- Acts as the Kerberos server for the MYCO.COM realm.
- The Kerberos server's fully qualified host name is kdc1.myco.com
Client PCs
- Run Windows 2000.
- PC used to administer network authentication service has the following
products installed:
- iSeries Access for Windows (5722-XE1)
- iSeries Navigator and the Security and Network subcomponents
 The KDC server name, kdc1.myco.com, and the
hostname, iseriesa.myco.com are fictitious names used in this scenario.
The KDC server name, kdc1.myco.com, and the
hostname, iseriesa.myco.com are fictitious names used in this scenario.
Prerequisites and assumptions
- All system requirements, including software and operating system installation,
have been verified.To verify that the required licensed products have been installed, complete the following:
- In iSeries Navigator, expand .
- Ensure that all the necessary licensed products are installed.
- All necessary hardware planning and setup have been completed.
- TCP/IP and basic system security have been configured and tested on each of these servers.
- A single DNS server is used for host name resolution for the network.
Host tables are not used for host name resolution.Note: The use of host tables with Kerberos authentication may result in name resolution errors or other problems. For more detailed information about how host name resolution works with Kerberos authentication, see Host name resolution considerations.
Configuration steps
To configure network authentication service on your system, complete these steps.