You can use i5/OS™ packet filtering to route traffic between a partition and the outside network.
Network address translation (NAT) can route traffic between your virtual Ethernet network and the external network. This particular form of NAT is called static NAT, and it will allow both inbound and outbound IP traffic to and from the virtual Ethernet network. Other forms of NAT like masquerade NAT also work if your virtual Ethernet network does not need to receive traffic initiated by external clients. Like the TCP/IP routing and proxy ARP methods, you can take advantage of your existing i5/OS network connection. Since you will be using IP packet rules, you must use iSeries™ Navigator to create and apply your rules.
The following figure is an example of using NAT to connect your virtual Ethernet network to an external network. The 10.1.1.x network represents an external network while the 192.168.1.x network represents the virtual Ethernet network.
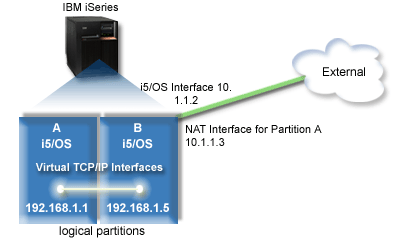
 In this example, any existing TCP/IP traffic for the server
runs over the 10.1.1.2 interface. A new interface 10.1.1.3
is created for communicating between the 10.1.1.x network and the 192.168.1.x
network. Because this is a static map scenario, the inbound traffic gets
translated from the 10.1.1.3 interface to the 192.168.1.5 interface.
The outbound traffic gets translated from the 192.168.1.5 interface
to the external 10.1.1.3 interface. Partition A and partition
B use their virtual interfaces 192.168.1.1 and 192.168.1.5 to
communicate with one another.
In this example, any existing TCP/IP traffic for the server
runs over the 10.1.1.2 interface. A new interface 10.1.1.3
is created for communicating between the 10.1.1.x network and the 192.168.1.x
network. Because this is a static map scenario, the inbound traffic gets
translated from the 10.1.1.3 interface to the 192.168.1.5 interface.
The outbound traffic gets translated from the 192.168.1.5 interface
to the external 10.1.1.3 interface. Partition A and partition
B use their virtual interfaces 192.168.1.1 and 192.168.1.5 to
communicate with one another.
To make static NAT work, you need to first set up your i5/OS and TCP/IP communications. Then you will create and apply some IP Packet rules. To configure virtual Ethernet to use the NAT method, complete these configuration tasks: