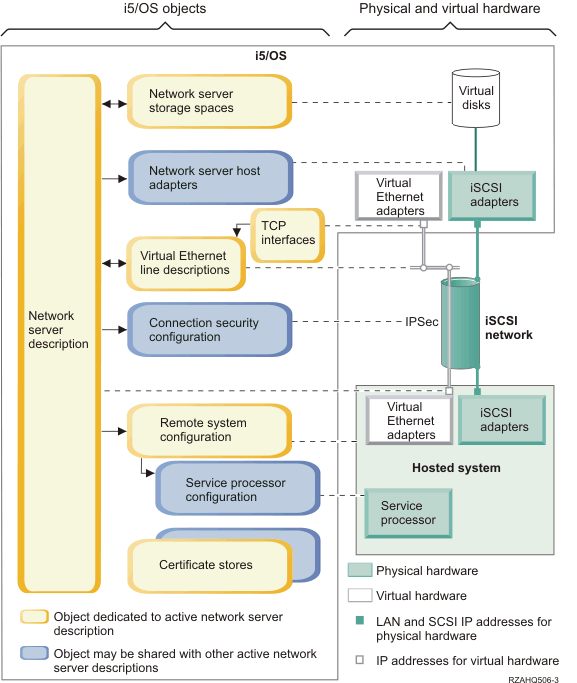

Since iSCSI attached servers can share a network with other systems, you may want to secure the iSCSI and service processor network connections. The following diagram shows the objects that i5/OS™ uses to configure network security for iSCSI attached servers.

Figure 16 shows key i5/OS objects as well as key hardware components that are used for iSCSI attached xSeries® or IBM® BladeCenter™ servers when network security is used.
See the following sections that describe the objects in Figure 16:
