View this scenario to learn how to configure your Management Central servers to participate in a single signon environment. After administrators complete the scenario for propagating a single signon configuration across multiple systems, they can do the necessary configuration so that their Management Central servers can participate in the single signon environment.
Situation
You are a system administrator for a medium-sized parts manufacturer. You have been using the iSeries™ Navigator Management Central server to manage a central server and three endpoint servers for the last three years. Your responsibilities include applying PTFs, creating new users on the network and other administrative duties. You have always liked having the ability to send and install PTFs to multiple systems from your central server; this saves you time. Your company has just upgraded to V5R4, and your company's security administrator has implemented a new security policy for your company, which requires user passwords to be different on each system in the network. Previously, the Management Central servers required that user profiles and passwords be identical across the network. You've learned that in i5/OS™ V5R4 that if you enable the Management Central servers for single signon, you no longer need to have matching user profiles and passwords on each endpoint system to use the Management Central server's functions. This limits the need to manage passwords on your i5/OS systems.
You completed the Scenario: Enable single signon for i5/OS for one of your new systems, and then you completed the Scenario: Propagate network authentication service and EIM across multiple systems. Now you want to want to configure all of your Management Central servers to participate in this single signon environment.
- Reduces administration of user profiles on central and endpoint systems.
- Reduces administrative password management for users on central and endpoint systems.
- Complies with the new company security policy, mandating that user passwords be unique on each system.
Objectives
You are one of three system administrators that work for your company. You and the other two administrators, Amanda and George, want to create a small single signon environment that decreases your administrative expense and simplifies your access to centrally managed applications and network assets.
- To comply with your company's new security policy by enabling the i5/OS V5R4 Management Central servers for single signon.
- To simplify password management by eliminating the need to have the same user profile and password on every endpoint system that is managed by the Management Central server.
- To allow all endpoint systems managed by the Management Central server to participate in a single signon environment.
- To ensure asset security within the enterprise by mapping users to EIM identifiers instead of using policy associations.
Details
The following figure illustrates the network environment for this scenario:
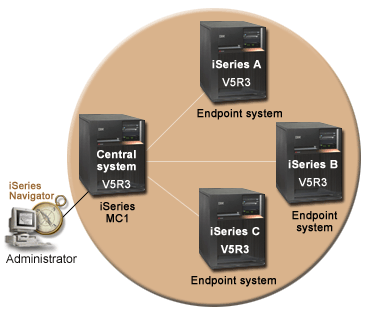
- Central system iSeriesMC1 (also specified as the model system):
- Runs i5/OS Version
5 Release 4 (V5R4) with the following options and licensed products installed:
- i5/OS Host Servers (5722-SS1 Option 12)
- i5/OS Access for Windows® (5722-XE1)
- Stores, schedules, and runs synchronize settings tasks for each of the endpoint systems.
- Configured for network authentication service and EIM.
- Selected model system from which the network authentication service and
EIM configurations are propagated to the target systems.Note: The model system should be configured similarly to the system identified as iSeries A in the Scenario: Create a single signon test environment. Refer to this scenario to ensure that all of the single signon configuration tasks on the model system are completed and verified.
- Runs i5/OS Version
5 Release 4 (V5R4) with the following options and licensed products installed:
- Endpoint systems iSeries A, iSeries B, and iSeries C:
- Runs i5/OS Version
5 Release 4 (V5R4) with the following options and licensed products installed:
- i5/OS Host Servers (5722-SS1 Option 12)
- iSeries Access for Windows (5722-XE1)
- Configured for network authentication service and EIM.
- Runs i5/OS Version
5 Release 4 (V5R4) with the following options and licensed products installed:
- Administrator's PC:
- Runs iSeries Access for Windows (5722-XE1).
- Runs iSeries Navigator with the
following subcomponents:
- Network
- Security
Note: Only required for PC used to administer network authentication service.
Prerequisites and assumptions
- Central system iSeriesMC1 (also specified as the model system):Note: This scenario assumes that the central system is properly configured for single signon. Refer to the Scenario: Create a single signon test environment to ensure that all of the single signon configuration tasks on the central system are completed and verified.
- All system requirements, including software and operating system installation,
have been verified. To verify that these licensed programs have been installed,
complete the following:
- In iSeries Navigator, expand your iSeries server→Configuration and Service→Software→Installed Products.
- Ensure that all the necessary licensed programs are installed.
- All necessary hardware planning and setup is complete.
- TCP/IP and basic system security are configured and tested.
- Secure Sockets Layer (SSL) has been configured to protect the transmission
of data between these servers.Note: When you propagate network configuration service configuration among servers, sensitive information like passwords are sent across the network. You should use SSL to protect this information, especially if it is being sent outside your Local Area Network (LAN). See Scenario: Secure all connections to your Management Central server with SSL for details.
- All system requirements, including software and operating system installation,
have been verified. To verify that these licensed programs have been installed,
complete the following:
- Endpoint systems iSeries A, iSeries B, and iSeries C:
- All system requirements, including software and operating system installation,
have been verified. To verify that these licensed programs have been installed,
complete the following:
- In iSeries Navigator, expand your iSeries server→Configuration and Service→Software→Installed Products.
- Ensure that all the necessary licensed programs are installed.
- All necessary hardware planning and setup is complete.
- TCP/IP and basic system security are configured and tested.
- Secure Sockets Layer (SSL) has been configured to protect the transmission
of data between these servers.Note: When you propagate network configuration service configuration among servers, sensitive information like passwords are sent across the network. You should use SSL to protect this information, especially if it is being sent outside your Local Area Network (LAN). See Scenario: Secure all connections to your Management Central server with SSL for details.
- All system requirements, including software and operating system installation,
have been verified. To verify that these licensed programs have been installed,
complete the following:
- You have already configured network authentication service and EIM on your central system and endpoint systems (seeScenario: Enable single signon for i5/OS and Scenario: Propagate network authentication service and EIM across multiple systems for information).
- You are using Microsoft® Windows Active Directory as a Kerberos server.
- You have already added i5/OS service principal names to the Kerberos server (you perform this task in Scenario: Enable single signon for i5/OS).
- You have already tested the network authentication services configuration (you perform this task in Scenario: Propagate network authentication service and EIM across multiple systems).