Use this example to learn how the search flow works for a lookup operation that returns a target user identity from specific identifier associations based on the known Kerberos principal.
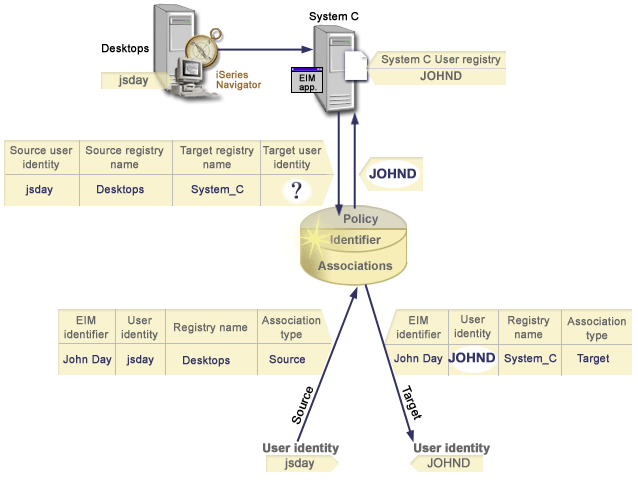
In Figure 12, an administrator wants to map a Windows® user in a Windows Active Directory registry to an i5/OS™ user profile. Kerberos is the authentication method that Windows uses and the name of the Windows Active Directory registry as the administrator defined it in EIM is Desktops. The user identity that the administrator wants to map from is a Kerberos principal named jsday. The name of the i5/OS registry as the administrator defined it in EIM is System_C and the user identity that the administrator wants to map to is a user profile named JOHND.
- A source association for the Kerberos principal named jsday in the Desktops registry.
- A target association for the i5/OS user profile named JOHND in the System_C registry.
Figure 12: EIM lookup operation returns a target user identity from specific identifier associations based on the known Kerberos principal jsday
| Source user identity and registry | ---> | EIM identifier | ---> | Target user identity |
|---|---|---|---|---|
| jsday in Desktops registry | ---> | John Day | ---> | JOHND (in System_C registry) |
The lookup operation search flows in this manner:
- The user jsday logs on and authenticates to Windows by means of his Kerberos principal in the Windows Active Directory registry Desktops.
- The user opens iSeries™ Navigator to access data on System_C.
- i5/OS uses an EIM API to perform an EIM lookup operation with a source user identity of jsday, a source registry of Desktops, and a target registry of System_C.
- The EIM lookup operation checks whether mapping lookups are enabled for the source registry Desktops and target registry System_C. They are.
- The lookup operation checks for a specific identifier source association that matches the supplied source user identity of jsday in a source registry of Desktops.
- The lookup operation uses the matching identifier source association to determine the appropriate EIM identifier name, which is John Day.
- The lookup operation uses this EIM identifier name to search for an identifier target association for the EIM identifier that matches the specified target EIM registry definition name of System_C.
- There is a such an identifier target association and the lookup operation returns the target user identity of JOHND as defined in the target association.
- With the mapping lookup operation complete, iSeries Navigator begins to run under the JOHND user profile. The user's authority to access resources and perform actions within iSeries Navigator is determined by the authority defined for the JOHND user profile rather than the authority defined for the jsday user identity.