Group access policies identify distinct user groups for a connection, and allow you to apply common connection attributes and security settings to the entire group. In combination with IP filtering, this allows you to permit and restrict access to specific IP addresses on your network.
Situation
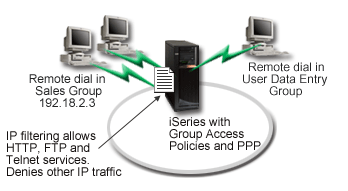
Your network has several groups of distributed users, each of whom need access to different resources on your corporate LAN. A group of data entry users needs access to the database and several other applications, while a people from other companies needs dial-up access to HTTP, FTP and Telnet services, but for security reasons must not be allowed access to other TCP/IP services or traffic. Defining detailed connection attributes and permissions for each user will duplicate your efforts, and providing network restrictions for all the users of this connection profile won't provide enough control. You'd like a way to define connection setting and permissions for several distinct groups of users who routinely dial into this server.
Solution
You need to apply unique IP filtering restrictions to two different groups of users. To accomplish this, you will create group access policies and IP filter rules. Group access policies reference IP filter rules, so you need to create your filter rules first. In this example, you need to create a PPP filter to include IP filter rules for the "IBM® Business Partner" Group Access Policy. These filter rules will permit HTTP, FTP and Telnet services, but restrict access to all other TCP/IP traffic and services through the iSeries™ server. This scenario only shows the filter rules needed for the sales group; however, you can also set up similar filters for the "Data Entry" group.
Finally, you need to create the group access policies (one per group) to define your group. Group access policies allow you to define common connection attributes to a group of users. By adding a Group Access Policy to a Validation list on the iSeries server, you can apply these connection settings during the authentication process. The group access policy specifies several settings for the user's session, including the ability to apply IP filtering rules that will restrict the IP addresses, and TCP/IP services available to a user during their session.
Sample configuration
- Create the PPP filter identifier and IP packet rules filters that specify
the permissions and restrictions for this Group Access Policy.
- In iSeries Navigator, expand .
- Click Receiver Connection Profiles, and select Group Access Policies.
- Right-click a predefined group listed in the right pane and select Properties.
Note: If you want to create a new group access policy, right-click Group Access Policies and select New Group Access Policies. Complete the General tab. Then select the TCP/IP Settings tab and continue with step e below.
- Select the TCP/IP Settings tab, and click Advanced.
- Select Use IP packet rules for this connection, and click Edit Rules File. This will start the IP Packet Rules Editor, and open the PPP filters packet rules file.
- Open the Insert menu, and select Filters to
add filter sets. Use the General tab to define the filter sets, and the Services
tab to define the service you are permitting, such as HTTP. The following
filter set, "services_rules," will permit HTTP, FTP and Telnet services. The
filter rules include an implicit default deny statement, restricting any TCP/IP
services or IP traffic not specifically permitted. Note: The IP addresses in the following example are globally routable, and are for example purposes only.
###The following 2 filters will permit HTTP (Web browser) traffic in & out of the system. FILTER SET services_rules ACTION = PERMIT DIRECTION = INBOUND SRCADDR % = * DSTADDR = 192.18.2.3 PROTOCOL = TCP DSTPORT = 80 SRCPORT % = * FRAGMENTS = NONE JRN = OFF FILTER SET services_rules ACTION = PERMIT DIRECTION = OUTBOUND SRCADDR % = 192.18.2.3 DSTADDR = * PROTOCOL = TCP DSTPORT = * SRCPORT = % 80 FRAGMENTS = NONE JRN = OFF ###The following 4 filters will permit FTP traffic in & out of the system. FILTER SET services_rules ACTION = PERMIT DIRECTION = INBOUND SRCADDR % = * DSTADDR = 192.18.2.3 PROTOCOL = TCP DSTPORT = 21 SRCPORT % = * FRAGMENTS = NONE JRN = OFF FILTER SET services_rules ACTION = PERMIT DIRECTION = OUTBOUND SRCADDR % = 192.18.2.3 DSTADDR = * PROTOCOL = TCP DSTPORT = * SRCPORT = % 21 FRAGMENTS = NONE JRN = OFF FILTER SET services_rules ACTION = PERMIT DIRECTION = INBOUND SRCADDR % = * DSTADDR = 192.18.2.3 PROTOCOL = TCP DSTPORT = 20 SRCPORT % = * FRAGMENTS = NONE JRN = OFF FILTER SET services_rules ACTION = PERMIT DIRECTION = OUTBOUND SRCADDR % = 192.18.2.3 DSTADDR = * PROTOCOL = TCP DSTPORT = * SRCPORT = % 20 FRAGMENTS = NONE JRN = OFF ###The following 2 filters will permit telnet traffic in & out of the system. FILTER SET services_rules ACTION = PERMIT DIRECTION = INBOUND SRCADDR % = * DSTADDR = 192.18.2.3 PROTOCOL = TCP DSTPORT = 23 SRCPORT % = * FRAGMENTS = NONE JRN = OFF FILTER SET services_rules ACTION = PERMIT DIRECTION = OUTBOUND SRCADDR % = 192.18.2.3 DSTADDR = * PROTOCOL = TCP DSTPORT = * SRCPORT % = 23 FRAGMENTS = NONE JRN = OFF - Open the Insert menu, and select Filter
Interface. Use the filter interface to create a PPP filter identifier,
and include the filter sets you've defined.
- On the General tab, enter permitted_services for the PPP filter identifier.
- On the Filter sets tab, select the filter set services_rules, and click Add.
- Click OK. The following line will be added to the rules file:
###The following statement binds (associates) the 'services_rules' filter set with the PPP filter ID "permitted_services." This PPP filter ID can then be applied to the physical interface associated with a PPP connection profile or Group Access Policy. FILTER_INTERFACE PPP_FILTER_ID = permitted_services SET = services_rules
- Save your changes, and exit. If you need to undo these changes later, use the character-based interface to enter the command: RMVTCPTBL *ALLThis will remove all filter rules and NAT on the server.
- On the Advanced TCP/IP settings dialog, leave the PPP filter identifier box blank, and click OK to exit. Later, you should apply the filter identifier you just created to a Group Access Policy, not this connection profile.
- Define a new Group Access policy for this user group.
- In iSeries Navigator, expand .
- Right click the Group Access Policy icon, and select New Group Access Policy. iSeries Navigator will display the New Group Access Policy definition dialog.
- On the General page, enter a name and description for the Group Access Policy.
- On the TCP/IP settings page:
- Select Use IP packet rules for this connection, and select the PPP filter identifier permitted_services.
- Select OK to save the Group Access Policy.
- Apply the Group Access Policy to the users associated with this group.
- Open the Receiver Connection Profile controlling these dial-up connections.
- On the Authentication page of the Receiver Connection Profile, select the validation list that contains the users' authentication information, and click Open.
- Select a user in the Sales group to which you want to apply the Group Access Policy, and click Open.
- Click Apply a Group Policy to the user, and select the Group Access Policy defined in step 2.
- Repeat for each Sales user.