In this scenario, you want to configure network authentication service and EIM to create a basic single signon test environment. Use this scenario to gain a basic understanding of what configuring a single signon environment involves on a small scale before implementing single signon across an entire enterprise.
Situation
You, John Day, are a network administrator for a large wholesale company. Currently you spend much of your time troubleshooting password and user identity problems, such as forgotten passwords. Your network is comprised of several iSeries™ systems and a Windows® 2000 server, where your users are registered in Microsoft® Windows Active Directory. Based on your research, you know that Microsoft Active Directory uses the Kerberos protocol to authenticate Windows users. You also know that the iSeries provides a single signon solution based on an implementation of Kerberos authentication, called network authentication service, in conjunction with EIM.
You are excited about the benefits of using single signon. However, you want to thoroughly understand single signon configuration and usage before you begin using it across your entire enterprise. Consequently, you decide to configure a test environment first.
After considering the various groups in your company, you decide to create the test environment for the Order Receiving department. The employees in the Order Receiving department use multiple applications on one iSeries system to handle incoming customer orders. Consequently, the Order Receiving department provides an excellent opportunity for you to create a single signon test environment that you can use to better understand how single signon works and how to plan a single signon implementation across your enterprise.
Scenario advantages
- Allows you to see some of the benefits of single signon on a small scale to better understand how you can take full advantage of it before you create a large-scale, single signon environment.
- Provides you with a better understanding of the planning process you need to use to successfully and to more quickly implement single signon across your entire enterprise.
- Minimizes the learning curve of implementing single signon across your enterprise.
Objectives
As the network administrator at MyCo, Inc., you want to create a small single signon environment for testing that includes a small number of users and a single iSeries system. You want to perform thorough testing to ensure that user identities are correctly mapped within your test environment. Based on this configuration, you eventually want to expand the test environment to include the other systems and users in your enterprise.
The objectives of this scenario are as follows:
- The iSeries system, known as iSeries A, must be able to use Kerberos within the MYCO.COM realm to authenticate the users and services that are participating in this single signon test environment. To enable the system to use Kerberos, iSeries A must be configured for network authentication service.
- The directory server on iSeries A
must function as the domain controller for the new EIM domain.Note: Refer to Domains to learn how an EIM domain and a Windows 2000 domain both fit into the single signon environment.
- One user profile on iSeries A and one Kerberos principal must each be mapped to a single EIM identifier.
- A Kerberos service principal must be used to authenticate the user to the iSeries Access for Windows applications.
Details
The following figure illustrates the network environment for this scenario.
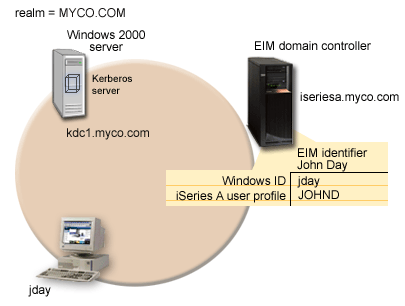
The figure illustrates the following points relevant to this scenario.
EIM domain data defined for the enterprise
- An EIM registry definition for iSeries A called ISERIESA.MYCO.COM.
- An EIM registry definition for the Kerberos registry called MYCO.COM.
- An EIM identifier called John Day. This identifier uniquely identifies John Day, the administrator for MyCo.
- A source association for the jday Kerberos principal on the Windows 2000 server.
- A target association for the JOHND user profile on iSeries A.
Windows 2000 server
- Acts as the Kerberos server (kdc1.myco.com), also known as a key distribution center (KDC), for the network.
- The default realm for the Kerberos server is MYCO.COM.
- A Kerberos principal of jday is registered with the Kerberos server on the Windows 2000 server. This principal will be used to create a source association to the EIM identifier, John Day.
iSeries A
- Runs i5/OS™ Version
5 Release 4 (V5R4) with the following options and licensed products installed:
- i5/OS Host Servers (5722-SS1 Option 12)
- Qshell Interpreter (5722-SS1 Option 30)
- iSeries Access for Windows (5722-XE1)
Note: You can implement this scenario using a server that runs OS/400® V5R2 or i5/OS V5R3. However, some of the configuration steps will be slightly different due to i5/OS V5R4 enhancements. - The IBM® Directory Server for iSeries (LDAP) on iSeries A will be configured to be the EIM domain controller for the new EIM domain, MyCoEimDomain.
- iSeries A participates in the EIM domain, MyCoEimDomain.
- The principal name for iSeries A is krbsvr400/iseriesa.myco.com@MYCO.COM.
- The user profile of JOHND exists on iSeries A. You will create a target association between this user profile and the EIM identifier, John Day.
- The home directory for the i5/OS user profile, JOHND, (/home/JOHND) is defined on iSeries A.
Client PC used for single signon administration
- Runs Microsoft Windows 2000 operating system.
- Runs i5/OS V5R4 iSeries Access for Windows (5722-XE1).
- Runs iSeries Navigator with the
following subcomponents installed:
- Network
- Security
- Serves as the primary logon system for administrator John Day.
- Configured to be part of the MYCO.COM realm (Windows domain).
Prerequisites and assumptions
Successful implementation of this scenario requires that the following assumptions and prerequisites are met:
- All system requirements, including software and operating system installation,
have been verified.To verify that the licensed programs have been installed, complete the following:
- In iSeries Navigator, expand .
- Ensure that all the necessary licensed programs are installed.
- All necessary hardware planning and setup is complete.
- TCP/IP and basic system security are configured and tested on each system.
- The directory server and EIM should not be previously configured on iSeries A.Note: Instructions in this scenario are based on the assumption that the directory server has not been previously configured on iSeries A. However, if you already configured the directory server, you can still use these instructions with only slight differences. These differences are noted in the appropriate places within the configuration steps.
- A single DNS server is used for host name resolution for the network.
Host tables are not used for host name resolution.Note: The use of host tables with Kerberos authentication may result in name resolution errors or other problems..