Use this example to learn how the search flow works for a lookup operation that returns a target user identity from specific identifier associations based on the known user identity.
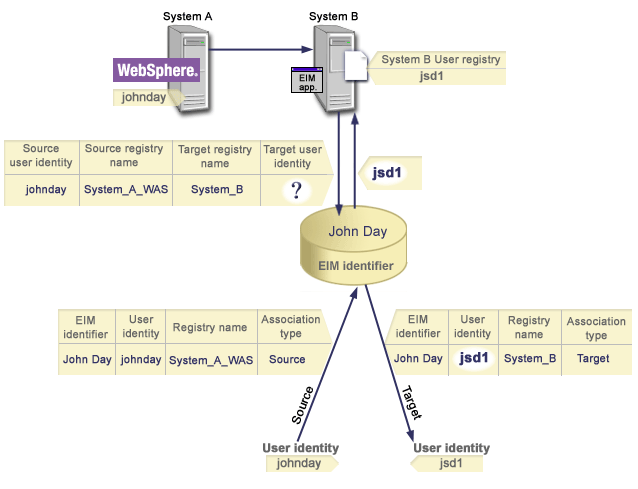
In Figure 11, the user identity johnday authenticates to the WebSphere® Application Server by using Lightweight Third-Party Authentication (LPTA) on System A. The WebSphere Application Server on System A calls a integrated program on System B to access data on System B. The integrated program uses an Enterprise Identity Mapping (EIM) API to perform an EIM lookup operation based on the user identity on System A as the source of the operation. The application supplies the following information to perform the operation: johnday as the source user identity, System_A_WAS as the source EIM registry definition name, and System_B as the target EIM registry definition name. This source information is passed to EIM and the EIM lookup operation finds an identifier source association that matches the information. Using the EIM identifier name John Day, the EIM lookup operation searches for an identifier target association for this identifier that matches the target EIM registry definition name for System_B. When the matching target association is found, the EIM lookup operation returns the jsd1 user identity to the application.
Figure 11: EIM lookup operation returns a target user identity from specific identifier associations based on the known user identity johnday