The goal of this advisor is to provide you with a basic understanding of the information you will need to configure VPN on your iSeries(TM). This advisor assumes that you are familiar with your network and the applications that power your business. You will also need to know the role of your iSeries as it pertains to the IP traffic in your network. For example, if your iSeries routes IP traffic for a LAN, you will configure your iSeries as a VPN gateway. Or, if your iSeries hosts an application that must communicate securely with another system, you will configure your iSeries as a VPN host.
Before you begin, it would be helpful to review the basic VPN concepts described in the Virtual private networking topic of the iSeries Information Center. In addition, you should be familiar with your network, the applications that you use, and your network security policy. For instance, if your iSeries is a VPN gateway, you need to ensure that the IP traffic routes through it. VPNs can play an important role in safeguarding IP traffic, but you must also consider protecting your intranet by firewall or other mechanisms.
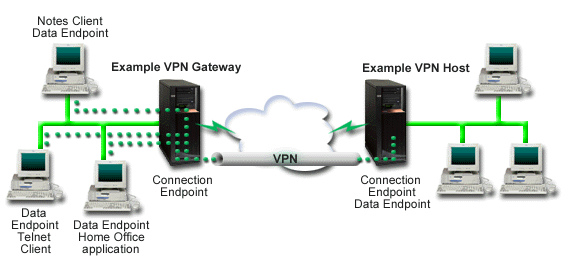
Consider these questions about your system, and the one with which you will connect:The diagram below shows an example VPN gateway on the left side of the connection and an example VPN host on the right.
Important note:
This diagram shows the iSeries computers attached directly to the Internet. The absence of a firewall is intended to simplify the example. It does not imply that the use of a firewall is not necessary. In fact, you should consider the security risks involved any time you connect to the Internet. The work sheet at the end of this advisor lists several IBM(R) Redbooks(TM) that you should refer to for detailed descriptions of various methods for reducing these risks.

After you implement your VPN, file a printed copy of the planning work sheet with your other network security information.