In this scenario, your company uses IP filtering to restrict the IP traffic that can access its Web server to HTTP, Telnet, and FTP.
Situation
You want to provide Web applications to your customers, but your current firewall is working overtime and you do not want to add additional stress to it. Your colleague suggests running the applications outside of the firewall. However, from the Internet, you only want HTTP, FTP, and Telnet traffic to have access to your iSeries™ Web server. What should you do?
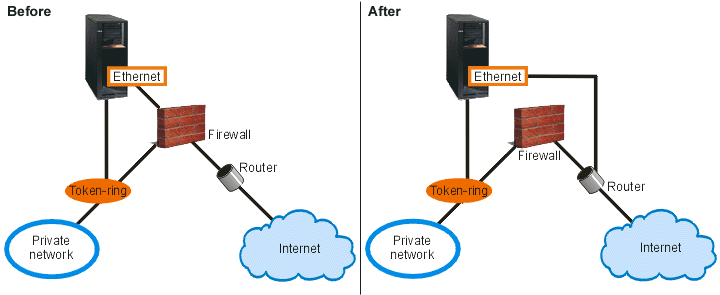
Solution
IP filtering allows you to set rules that define what information you want to permit. In this scenario you will write filter rules that permit HTTP, FTP, and Telnet traffic (inbound and outbound) to the Web server, which is your iSeries server in this case. The public address of the server is 192.54.5.1, and the private IP address is 10.1.2.3.
Configuration
- The type of service you want to permit: HTTP
- The public address of the iSeries server: 192.54.5.1
- The address of the client: Any IP address
- The interface over which the service will run: TRNLINE
- The direction the service will run: INBOUND
- The name you want to use to identify this filter set: external_files
To use the Permit Service wizard, follow these steps:
- In iSeries Navigator, select .
- Right-click Packet Rules, and select Rules Editor.
- From the Welcome Packet Rules Configuration dialog, select Create a new packet rules file, and click OK.
- From the Wizards menu, select Permit A Service, and follow the wizard's instructions to create the filter rules.
These packet rules permit HTTP traffic in and out of the system. The packet rules looks like the following example:
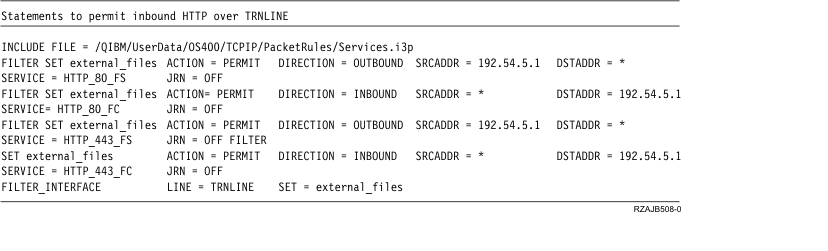
Use the Permit a Service wizard two more times to create filter rules that permit FTP traffic and Telnet traffic in and out of the system.
After you finish creating these filter rules, verify them to ensure that they will activate without errors. After that, you can activate them.