For more information about trust association interceptors, see Trust associations.
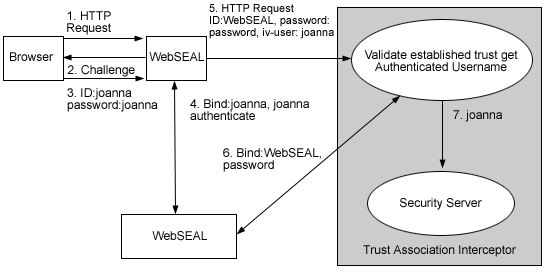
A typical scenario where the trust association interceptor (TAI) is used is better understood based on an environment where IBM Tivoli WebSEAL product is deployed and used with WebSphere Application Server. For WebSEAL, there is an implementation of the TAI already provided with the product. These steps outline the typical flow of an HTTP request for a secured WebSphere Application Server resource authenticated by WebSEAL, through a Web trust association.
Note: Versions 3.9 and higher of WebSEAL do not send the user ID and password to the server. Trust is based on a mutual secure sockets layer connection established between WebSEAL and the WebSphere Application Server. As a result, steps 6 and 7 do not apply to versions 3.9 and higher of WebSEAL.

When you set up security for the first time, you need to complete the following steps if you want to use WebSEAL Trust Association Interceptor or your own trust association interceptor with a reverse proxy security server.
Perform these steps in the WebSphere administrative console:
In the topology tree, expand Security --> Authentication mechanisms and click LTPA.
Click Trust Association under Additional Properties.
Select the Trust Association Enabled check box.
Click Interceptors under Additional Properties.
Select the interceptor that you want to configure. For additional information, see Trust association interceptor settings. ![]()
To configure an interceptor, click the interceptor classname.
Click Custom Properties.
On the Custom Properties page, click New.
Specify the property name and value pairs. These are the name and value pairs for WebSEAL:
| Property name | Value |
|---|---|
| com.ibm.websphere.security.trustassociation.types | WebSEAL |
| com.ibm.websphere.security.webseal.loginID | The ID of the WebSEAL server. |
| com.ibm.websphere.security.webseal.id | iv-user. This is a special header field that is sent by WebSEAL with the request to WebSphere Application Server. |
| com.ibm.websphere.security.webseal.hostnames | The host names (case sensitive) that are expected in the request header (the VIA header). This should also include the proxy host names (if any) unless the com.ibm.websphere.security.webseal.ignoreProxy is set to true. |
| com.ibm.websphere.security.webseal.ports | The corresponding port number of the host names that are expected in the request header (the VIA header). This should also include the proxy ports (if any) unless the com.ibm.websphere.security.webseal.ignoreProxy is set to true. |
| com.ibm.websphere.security.webseal.ignoreProxy | An optional property that if set to true or yes ignores the proxy host names and ports in the VIA header. By default this property is set to false. |
Click OK.
Save the configuration.