This scenario describes a company that wants to sign objects that it packages and distributes to multiple systems. Based on the company's business needs and security goals, this scenario describes how to use iSeries™ Navigator's Management Central function to package and sign objects that they distribute to other systems.
Situation
Your company (MyCo, Inc.) develops applications that it distributes to multiple systems in multiple locations within the company. As the network administrator, you are responsible for ensuring that these applications are installed and updated on all company servers. You currently use iSeries Navigator's Management Central function to more easily package and distribute these applications and to perform other administrative tasks for which you are responsible. However, you spend more time than you like tracking down and correcting problems with these applications because of unauthorized changes to objects. Consequently, you want to better secure the integrity of these objects by digitally signing them.
You have researched i5/OS™ object signing capabilities and have learned that, beginning in V5R2, Management Central allows you to sign objects when you package and distribute them. By using Management Central you can meet your company's security goals efficiently and relatively easily. You also decide to create a Local Certificate Authority (CA) and use it to issue a certificate to sign objects. Using a certificate issued by a Local CA for object signing limits the expense of using this security technology because you do not need to purchase a certificate from a public well-known CA.
This example serves as a useful introduction to the steps involved in configuring and using object signing for applications that you distribute to multiple company systems.
Scenario advantages
- Using Management Central to package and sign objects reduces the amount of time that you must spend to distribute signed objects to your company's servers.
- Using Management Central to sign objects in a package decreases the number of steps that you must perform to sign objects because the signing process is part of the packaging process.
- Signing a package of objects allows you to more easily determine whether objects have been changed after they have been signed. This may reduce some of the troubleshooting that you do in the future to track down application problems.
- Using a certificate issued by a Local Certificate Authority (CA) to sign objects makes signing objects less expensive to implement.
Objectives
In this scenario, MyCo, Inc. wants to digitally sign applications that it distributes to multiple systems within the company. As the network administrator at MyCo, Inc, you already use Management Central for a number of administrative tasks. Consequently, you want to extend your current use of Management Central to sign the company applications that you distribute to other systems.
The objectives for this scenario are as follows:
- Company applications must be signed with a certificate issued by a Local CA to limit the costs of signing applications.
- System administrators and other designated users must be able to easily verify digital signatures on all servers to verify the source and authenticity of company signed objects. To accomplish this, each server must have a copy of both the company's signature verification certificate and the Local Certificate Authority (CA) certificate in each server's *SIGNATUREVERIFICATION certificate store.
- Verifying the signatures on company applications allows administrators and others to detect whether the content of the objects has changed since they were signed.
- Administrators must be able to use Management Central to package, sign, and then distribute their applications to their systems.
Details
The following figure illustrates the object signing and signature verification process for implementing this scenario:
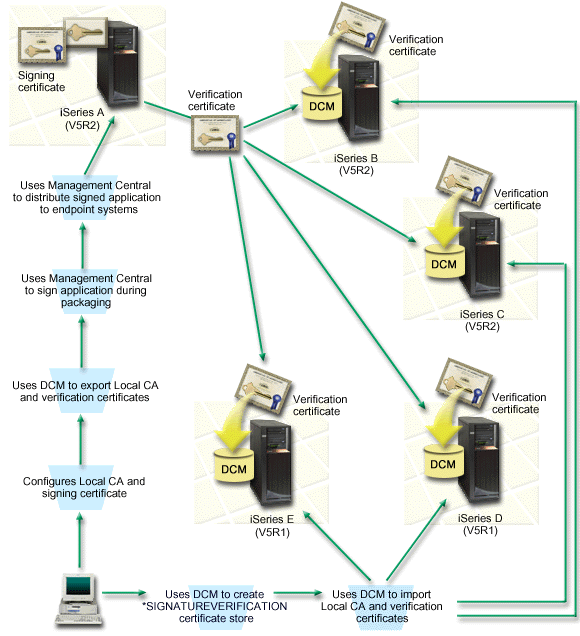
The figure illustrates the following points relevant to this scenario:
Central system (System A)
- System A runs i5/OS Version 5 Release 2 (V5R2).
- System A serves as the central system from which Management Central functions run, including packaging and distributing company applications.
- System A has a Cryptographic Access Provider 128-bit for iSeries (5722–AC3) installed.
- System A has Digital Certificate Manager (i5/OS option 34) and the IBM® HTTP Server (5722–DG1) installed and configured.
- System A acts as the Local Certificate Authority (CA) and the object signing certificate resides on this system.
- System A is the primary object signing system for company applications.
Product object signing for customer distribution is accomplished on System
A by performing these tasks:
- Using DCM to create a Local CA and using the Local CA to create an object signing certificate.
- Using DCM to export a copy of the Local CA certificate and the signature verification certificate to a file so that endpoint systems (System B, C, D, and E) can verify signed objects.
- Using Management Central to sign application objects and package them with the verification certificate files.
- Using Management Central to distribute signed application and certificate files to endpoint systems.
Endpoint systems (Systems B, C, D, and E)
- System B and C run i5/OS Version 5 Release 2 (V5R2).
- Sysetm D and E run i5/OS Version 5 Release 1 (V5R1).
- System B, C, D, and E have Digital Certificate Manager (option 34) and IBM HTTP Server (5722–DG1) installed and configured.
- System B, C, D, and E receive a copy of both the company's signature verification certificate and the Local CA from the central system (System A) when the systems receive the signed application.
- DCM is used to create the *SIGNATUREVERIFICATION certificate store and import the Local CA and verification certificates into this certificate store.
Prerequisites and assumptions
This scenario depends on the following prerequisites and assumptions:
- All systems meet the requirements for installing and using Digital Certificate Manager (DCM).
- No one has previously configured or used DCM on any of the systems.
- System A meets the requirements for installing and using iSeries Navigator and Management Central.
- The Management Central server must be running on all endpoint systems.
- All systems have the highest level of Cryptographic Access Provider 128-bit licensed program (5722-AC3) installed.
- The default setting for the verify object signatures during restore (QVFYOBJRST) system value on all scenario systems is 3 and has not been changed from this setting. The default setting ensures that the server can verify object signatures as you restore the signed objects.
- The network administrator for System A must have *ALLOBJ user profile special authority to sign objects, or the user profile must be authorized to the object signing application.
- The network administrator or anyone else who creates a certificate store in DCM must have *SECADM and *ALLOBJ user profile special authorities.
- System administrators or others on all other systems must have *AUDIT user profile special authority to verify object signatures.
Configuration task steps
There are two sets of tasks that you must complete to implement this scenario: One set of tasks allows you to set up System A to use Management Central to sign and distribute applications. The other set of tasks allows system administrators and others to verify the signatures on these applications on all other servers. Refer to the scenario details topic below for the steps to complete these tasks.
Object signing task steps
To sign objects as described in this scenario, refer to the scenario details topic below for steps to complete each of the following tasks on System A :
- Complete all prerequisite steps to install and configure all needed iSeries products
- Use DCM to create a Local Certificate Authority (CA) to issue a private object signing certificate.
- Use DCM to create an application definition.
- Use DCM to assign a certificate to the object signing application definition
- Use DCM to export the certificates that other systems must use for verifying object signatures You must export both a copy of the Local CA certificate and a copy of the object signing certificate as a signature verification certificate to a file.
- Transfer the certificate files to each endpoint system on which you intend to verify signatures.
- Use iSeries Navigator Management Central to sign the application objects
Signature verification task steps
You need to complete these signature verification configuration tasks on each endpoint system before you use Management Central to transfer the signed application objects to them. Signature verification configuration must be completed before you can successfully verify signatures as you restore the signed objects on the endpoint systems.
On each endpoint system, you must complete these tasks to verify signatures on objects as this scenario describes:
- Use DCM to create the *SIGNATUREVERIFICATION certificate store
- Use DCM to import the Local CA certificate and the signature verification certificate