Use this example to learn how the search flow works for a lookup operation that returns a target user identity from a default registry policy association.
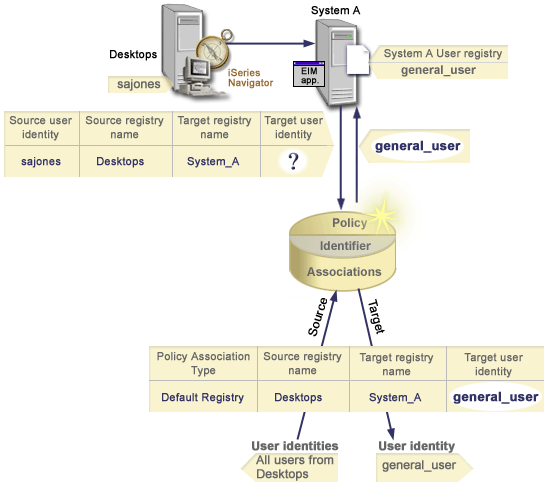
In Figure 13, an administrator wants to map all desktop workstation users in a Windows® Active Directory registry to a single i5/OS™ user profile named general_user in an i5/OS registry that he named System_A in Enterprise Identity Mapping (EIM). Kerberos is the authentication method that Windows uses and the name of the Windows Active Directory registry as the administrator defined it in EIM is Desktops. One of the user identities that the administrator wants to map from is a Kerberos principal named sajones.
The administrator creates a default registry policy association with the following information:
- A source registry of Desktops.
- A target registry of System_A.
- A target user identity of general_user.
Figure 13: A lookup operation returns a target user identity from a default registry policy association.
| Source user identity and registry | ---> | Default registry policy association | ---> | Target user identity |
|---|---|---|---|---|
| sajones in Desktops registry | ---> | Default registry policy association | ---> | general_user (in System_A registry) |
The lookup operation search flows in this manner:
- The user sajones logs on and authenticates to her Windows desktop by means of her Kerberos principal in the Desktops registry.
- The user opens iSeries™ Navigator to access data on System A.
- i5/OS uses an EIM API to perform an EIM lookup operation with a source user identity of sajones, a source registry of Desktops, and a target registry of System_A.
- The EIM lookup operation checks whether mapping lookups are enabled for the source registry Desktops and target registry System_A. They are.
- The lookup operation checks for a specific identifier source association that matches the supplied source user identity of sajones in a source registry of Desktops. It does not find a matching identifier association.
- The lookup operation checks whether the domain is enabled to use policy associations. It is.
- The lookup operation checks whether the target registry (System_A) is enabled to use policy associations. It is.
- The lookup operation checks whether the source registry (Desktops) is an X.509 registry. It is not.
- The lookup operation checks whether there is a default registry policy association that matches the source registry definition name (Desktops) and the target registry definition name (System_A).
- The lookup operation determines that there is one and returns general_user as the target user identity.
Sometimes an EIM lookup operation returns ambiguous results. This can happen, for example, when more than one target user identity matches the specified lookup operation criteria. Some EIM-enabled applications, including i5/OS applications and products are not designed to handle these ambiguous results and may fail or give unexpected results. You may need to take action to resolve this situation. For example, you may need to either change your EIM configuration or define lookup information for each target user identity to prevent multiple matching target user identities. Also, you can test a mapping to determine whether the changes you make work as expected.