This example depicts Domain Name System (DNS) operating over a firewall to protect internal data from the Internet, while allowing internal users to access data on the Internet.
The following illustration depicts a simple subnet network that uses a firewall for security. OS/400® V5R1 DNS based on BIND 8 allows you to set up multiple DNS servers on a single iSeries™. Suppose that the company has an internal network with reserved IP space, and an external section of a network that is available to the public.
The company wants its internal clients to be able to resolve external host names and to exchange mail with people on the outside. The company also wants its internal resolvers to have access to certain internal-only zones that are not available at all outside of the internal network. However, they do not want any outside resolvers to be able to access the internal network.
To accomplish this, the company sets up two DNS server instances on the same iSeries server, one for the intranet and one for everything in its public domain. This is called split DNS.
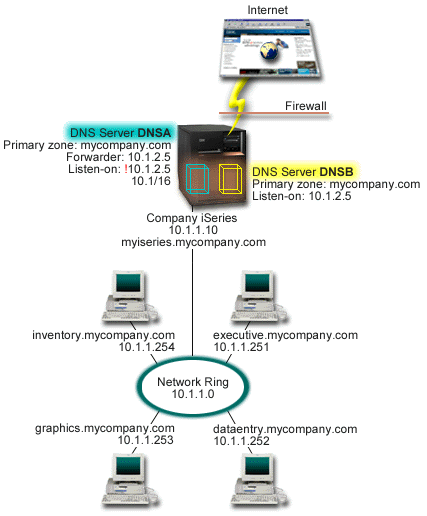
The external server, DNSB, is configured with a primary zone mycompany.com. This zone data includes only the resource records that are intended to be part of the public domain. The internal server, DNSA, is configured with a primary zone mycompany.com, but the zone data defined on DNSA contains intranet resource records. The forwarders option is defined as 10.1.2.5. This forces DNSA to forward queries it cannot resolve to the DNSB server.
If you are concerned about the integrity of your firewall or other security threats, you have the option of using the listen-on option to help protect internal data. To do this, you can configure the internal server to only allow queries to the internal mycompany.com zone from internal hosts. In order for all this to work properly, internal clients need to be configured to query only the DNSA server. You need to consider the following configuration settings to set up split DNS:
- Listen-on
In previous examples, there has been only one DNS server on an iSeries. It is set to listen on all interface IP addresses. Whenever you have multiple DNS servers on an iSeries, you have to define the interface IP addresses that each one listens on. Two DNS servers cannot listen on the same address. In this case, assume that all queries coming in from the firewall are sent in on 10.1.2.5. These queries should be sent to the external server. Therefore, DNSB is configured to listen on 10.1.2.5. The internal server, DNSA, is configured to accept queries from anything on the 10.1.x.x interface IP addresses except 10.1.2.5. To effectively exclude this address, the Address Match List (AML) must have the excluded address listed before the included address prefix.
- Address Match List (AML) order
The first element in the AML that a given address matches is used. For example, to allow all addresses on the 10.1.x.x network except 10.1.2.5, the ACL elements must be in the order (!10.1.2.5; 10.1/16). In this case, the address 10.1.2.5 is compared to the first element and will immediately be denied.
If the elements are reversed (10.1/16; !10.1.2.5), the IP address 10.1.2.5 will be allowed access because the server will compare it to the first element, which matches, and allow it without checking the rest of the rules.