This scenario demonstrates how you can implement a firewall using a guest partition running Linux®.
Situation
You are the system administrator of a company that has just consolidated your company's workload to a new iSeries™ server. Your new iSeries configuration has four partitions. You are running in a supported mixed environment with i5/OS™ partitions and guest partitions running Linux. You have a separate system with a firewall installed to protect the corporate network from untrusted data. However, that system is outdated and very expensive to maintain. You still want to protect your network what should you do?
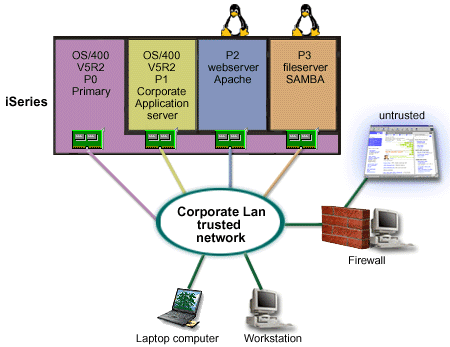
Solution using directly attached LAN adapters
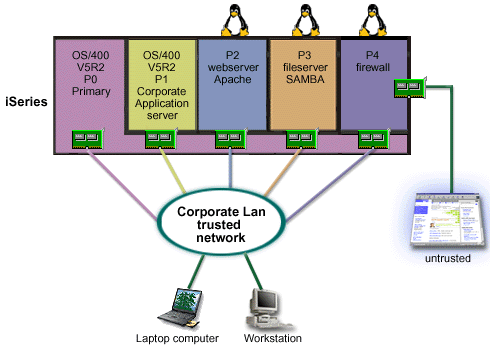
You had the hardware resources on your server to create another guest partition using iSeries Navigator. You installed Linux in partition P4. The firewall is built into the kernel that you are using. Your Linux firewall partition owns a directly attached LAN adapter that protects the entire system from untrusted data.
While your employees are able to use their laptop computers and workstations to connect to the trusted corporate network, you have the added assurance that your entire Corporate LAN is protected with your iSeries Linux firewall partition.
Solution using virtual Ethernet adapters
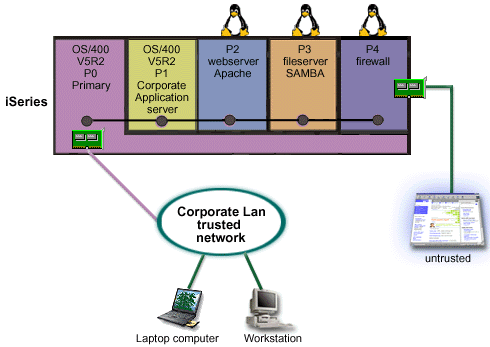
You created and installed Linux in a guest partition on your iSeries. However, you don't want to use a separate physical ethernet adapter for each partition, so you decide to use virtual ethernet to connect your partitions to the network. Your new Linux partition has a directly attached LAN adapter that connects your firewall to the untrusted network. Your primary partition owns a directly attached LAN adapter so your iSeries server can be connected to the trusted network. All of your partitions are able to communicate with each other and the Corporate Lan because they use virtual Ethernet.
Although you reduced the number of directly attached LAN adapters in this configuration, your entire network is still protected by the Linux firewall partition.