This scenario discusses how to enable single signon for your HTTP Server (powered by Apache).
 for more information.
for more information. To learn more about Kerberos and network security on the iSeries™, see Network authentication service.
This scenario discusses how to enable single signon for your HTTP Server (powered by Apache).
 for more information.
for more information. To learn more about Kerberos and network security on the iSeries™, see Network authentication service.
The JKL Web administrator, John Day, wants to enable single signon for the JKL Toy Company network. The network consists of several iSeries systems and a Windows® 2000 server, where the users are registered in Microsoft® Windows Active Directory. Based on John Day's research, he knows that Microsoft Active Directory uses the Kerberos protocol to authenticate Windows users. John Day also knows that i5/OS™ provides a single signon solution based on an implementation of Kerberos authentication, called network authentication service, in conjunction with Enterprise Identity Mapping (EIM).
While excited about the benefits of a single signon environment, John Day wants to thoroughly understand single signon configuration and usage before using it across the entire enterprise. Consequently, John Day decides to configure a test environment first.
After considering the various groups in the company, John Day decides to create the test environment for the MYCO Order Receiving department, a subsidiary of JKL Toys. The employees in the Order Receiving department use multiple applications, including HTTP Server, on one iSeries system to handle incoming customer orders. John Day uses the Order Receiving department as a testing area to create a single signon test environment that can be used to better understand how single signon works and how to plan a single signon implementation across the JKL enterprise.
This scenario has the following advantages:
As the network administrator at JKL Toy Company, John Day wants to create a small single signon test environment that includes a small number of users and a single iSeries server, iSeries A. John Day wants to perform thorough testing to ensure that user identities are correctly mapped within the test environment. The first step is to enable a single signon environment for i5/OS and applications on iSeries A, including the HTTP Server (powered by Apache). After implementing the configuration successfully, John Day eventually wants to expand the test environment to include the other systems and users in the JKL enterprise.
The objectives of this scenario are as follows:
Note: Two types of domains play key roles in the single signon environment: an EIM domain and a Windows 2000 domain. Although both of these terms contain the word domain, these entities have very different definitions.
Use the following descriptions to understand the differences between these two types of domains. For more information about these terms, see the EIM and Network authentication service topics.
A realm is a collection of machines and services. The main purpose of a realm is to authenticate clients and services. Each realm uses a single Kerberos server to manage the principals for that particular realm.
Microsoft Windows Active Directory is an LDAP server that resides on the Windows 2000 server along with the Kerberos server. The Active Directory is used to store and manage the information in a Kerberos user registry. Microsoft Windows Active Directory uses Kerberos authentication as its default security mechanism. Therefore, if you are using Microsoft Active Directory to manage your users, you are already using Kerberos technology.
The following figure illustrates the network environment for this scenario:
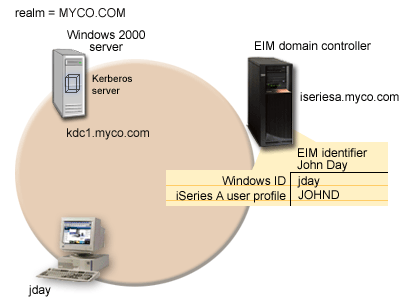
The figure illustrates the following points relevant to this scenario.
EIM domain data defined for the enterprise
Windows 2000 server
iSeries A
Client PC used for single signon administration
Successful implementation of this scenario requires that the following assumptions and prerequisites are met:
These are the configuration steps John Day completed. Follow these configuration steps to enable a single signon environment for your iSeries server.
The following planning work sheets are tailored to fit this scenario. These planning work sheets demonstrate the information that you need to gather and the decisions you need to make to prepare the single signon implementation described by this scenario. To ensure a successful implementation, you must be able to answer Yes to all prerequisite items in the work sheet and be able to gather all the information necessary to complete the work sheets before you perform any configuration tasks.
| Prerequisite work sheet | Answers |
|---|---|
| Are you running OS/400 or i5/OS at version V5R2 or higher? | Yes |
Are the following options and licensed products installed
on iSeries A?
|
Yes |
| Have you installed an application that is enabled for
single signon on each of the PCs that will participate in the single signon
environment? Note: For this scenario, all of the participating PCs have iSeries
Access for Windows installed and iSeries A has the HTTP
Server for iSeries installed.
|
Yes |
Is iSeries Navigator installed on the administrator's
PC?
|
Yes |
Have you installed the latest iSeries Access for Windows
service pack? See iSeries Access  for the latest service pack. for the latest service pack. |
Yes |
| Do you, the administrator, have *SECADM, *ALLOBJ, and *IOSYSCFG special authorities? | Yes |
Do you have one of the following systems in the network
acting as the Kerberos server (also known as the KDC)? If yes, specify which
system.
|
Yes, Windows 2000 Server |
| Are all your PCs in your network configured in a Windows (R) 2000 domain? | Yes |
| Have you applied the latest program temporary fixes (PTFs)? | Yes |
| Is the iSeries system time within 5 minutes of the system time on the Kerberos server? If not see Synchronize system times. | Yes |
You need this information to configure EIM and network authentication service to create a single signon test environment.
| Configuration planning work sheet for iSeries A | Answers |
|---|---|
How do you want to configure EIM for your system?
|
Create and join a new domain Note: This will configure
the directory server on the same system on which you are currently configuring
EIM.
|
| Do you want to configure network authentication service? Note: You
must configure network authentication service to configure single signon.
|
Yes |
| The Network Authentication Service wizard
launches from the EIM Configuration wizard. Use the following information
to complete the Network Authentication Service wizard: Note: You can launch
the Network Authentication Service wizard independently of the EIM Configuration
wizard.
|
|
| What is the name of the Kerberos default realm to which
your iSeries will belong? Note: A Windows 2000 domain is similar to a Kerberos
realm. Microsoft Windows Active Directory uses Kerberos authentication as
its default security mechanism.
|
MYCO.COM |
| Are you using Microsoft Active Directory? | Yes |
| What is the Kerberos server, also known as a key distribution center (KDC), for this Kerberos default realm? What is the port on which the Kerberos server listens? |
Note: This is the default port for the Kerberos server.
|
| Do you want to configure a password server for this
default realm? If yes, answer the following questions: What is name of the password server for this Kerberos server? What is the port on which the password server listens? |
Yes
Note: This is the default port for the Kerberos server.
|
For which services do you want to create keytab entries?
|
i5/OS Kerberos Authentication Note: A keytab entry for
HTTP Server must be done manually as described later in the configuration
steps.
|
| What is the password for your service principal or principals? | iseriesa123 Note: Any and all passwords
specified in this scenario are for example purposes only. To prevent a compromise
to your system or network security, never use these passwords as part of your
own configuration.
|
| Do you want to create a batch file to automate adding the service principals for iSeries A to the Kerberos registry? | Yes |
| Do you want to include passwords with the i5/OS service principals in the batch file? | Yes |
| As you exit the Network Authentication Service wizard, you will return to the EIM Configuration wizard. Use the following information to complete the EIM Configuration wizard: | |
| Specify user information for the wizard to use when
configuring the directory server. This is the connection user. You must specify
the port number, administrator distinguished name, and a password for the
administrator. Note: Specify the LDAP administrator's distinguished name (DN)
and password to ensure the wizard has enough authority to administer the EIM
domain and the objects in it.
|
Note: Any and all passwords specified in this scenario are for example
purposes only. To prevent a compromise to your system or network security,
do not use these passwords as part of your own configuration.
|
| What is the name of the EIM domain that you want to create? | MyCoEimDomain |
| Do you want to specify a parent DN for the EIM domain? | No |
| Which user registries do you want to add to the EIM domain? | Local i5/OS--ISERIESA.MYCO.COM Kerberos--MYCO.COM Note: The
Kerberos principals stored on the Windows 2000 server are not case sensitive;
therefore do not select Kerberos user identities are case sensitive.
|
| Which EIM user do you want iSeries A to use when performing
EIM operations? This is the system user Note: If you have not configured the
directory server prior to configuring single signon, the only distinguished
name (DN) you can provide for the system user is the LDAP administrator's
DN and password.
|
Note: Any and all passwords specified in this scenario are for example
purposes only. To prevent a compromise to your system or network security,
never use these passwords as part of your own configuration.
|
| After you complete the EIM Configuration wizard, use the following information to complete the remaining steps required for configuring single signon: | |
| What is the i5/OS user profile name for the user? | JOHND |
| What is the name of the EIM identifier that you want to create? | John Day |
| What kinds of associations do you want to create? |
|
| What is the name of the user registry that contains the Kerberos principal for which you are creating the source association? | MYCO.COM |
| What is the name of the user registry that contains the i5/OS user profile for which you are creating the target association? | ISERIESA.MYCO.COM |
You need to create a basic single signon configuration using the iSeries Navigator. The EIM configuration wizard will assist in the configuration process. Use the information from your planning work sheets to configure EIM and network authentication service on iSeries A.
To add the iSeries system to the Windows 2000 KDC, use the documentation for your KDC that describes the process of adding principals. By convention, the iSeries system name can be used as the username. Add the following principal names to the KDC:
krbsvr400/iSeriesA.ordept.myco.com@ORDEPT.MYCO.COM HTTP/iseriesa.myco.com@MYCO.COM
On a Windows 2000 server, follow these steps:
You need keytab entries for authentication purposes as well as for generating the authorization identity. The network authentication service (the i5/OS implementation of the Kerberos protocol) wizard creates a keytab entry for iSeriesA, however a keytab for HTTP must be manually created. The wizard is only able to create keytab entries for the system and certain applications that the code is aware are Kerberos-enabled. The network authentication service wizard configures network authentication service (Kerberos) for you. The wizard is called by the EIM wizard if you have not already configure network authentication service on the system or if your network authentication service configuration is not complete.
The kinit command is used to initiate Kerberos authentication. A Kerberos ticket-granting ticket (TGT) is obtained and cached for the HTTP Server principal. Use kinit to perform the ticket exchange for the HTTP Server principal. The ticket is cached for reuse.
You need to create a directory in the /home directory to store your Kerberos credentials cache. To create a home directory, complete the following:
Now that you have completed the network authentication service configuration tasks for iSeries A, you need to test that your configuration. You can do this by requesting a ticket-granting ticket for the HTTP principal name, HTTP/iseriesa.myco.com.
To test the network authentication service configuration, complete these steps:
Now that you have performed the initial steps to create a basic single signon configuration, you can begin to add information to this configuration to complete your single signon test environment. You need to create the EIM identifier that you specified in Step 1: Planning work sheet. In this scenario, this EIM identifier is a name that uniquely identifies John Day in the enterprise.
To create an EIM identifier, follow these steps:
You must create the appropriate associations between the EIM identifier and the user identities that the person represented by the identifier uses. These identifier associations, when properly configured, enable the user to participate in a single signon environment.
In this scenario, you need to create two identifier associations for the John Day identifier:
Now that you have created the John Day identifier, you need to create both a source association and a target association for it.
To create a source association between the Kerberos principal jday identifier, follow these steps:
You must use Kerberos to authenticate before you can use iSeries Navigator to access iSeries A. Therefore, from your PC, you need to configure iSeries Access for Windows to use Kerberos authentication. Jay Day will use iSeries Access to monitor the status of the iSeries HTTP Server and monitor the other activities on the iSeries.
To configure iSeries Access for Windows applications to use Kerberos authentication, complete the following steps:
The iSeries server does not require mapping, per the EIM configuration, as it is not a signon-type entity. You do, however, have to add the iSeries server to an existing EIM domain.
After the basic test environment is working, John Day configures the HTTP Server to participate in the single signon environment. Once single signon is enabled, John Day can access the HTTP Server without being prompted for a user ID and password after signing on to the Windows environment
To set up Kerberos for your HTTP Server, complete the following steps:
Restart the HTTP Server (powered by Apache) instance to use your new Kerberos settings.
Your configuration file will now include new code for the Kerberos options you selected.
Processing requests using client's authority is Disable:
<Directory /> Order Deny,Allow Deny From all Require valid-user PasswdFile %%KERBEROS%% AuthType Kerberos </Directory>
Processing requests using client's authority is Enabled:
<Directory /> Order Deny,Allow Deny From all Require valid-user PasswdFile %%KERBEROS%% UserID %%CLIENT%% AuthType Kerberos </Directory>
Now that you finished this scenario, the only EIM user you have defined that EIM can use is the Distinguished Name (DN) for the LDAP administrator. The LDAP administrator DN that you specified for the system user on iSeries A has a high level of authority to all data on the directory server. Therefore, you might consider creating one or more DNs as additional users that have more appropriate and limited access control for EIM data. The number of additional EIM users that you define depends on your security policy's emphasis on the separation of security duties and responsibilities. Typically, you might create at least the two following types of DNs:
This EIM administrator DN provides the appropriate level of authority for an administrator who is responsible for managing the EIM domain. This EIM administrator DN could be used to connect to the domain controller when managing all aspects of the EIM domain by means of iSeries Navigator.
This user provides the appropriate level of access control required for the system user that performs EIM operations on behalf of the operating system.
To use Microsoft Internet Explorer to access a Kerberos protected resource, the Integrated Windows Authentication option must be enabled. To enable it, from Internet Explorer go to Tools > Internet options > Advanced tab and Enable Integrated Windows Authentication.