Two operational attributes can be used to query aggregate group membership. For a given group entry, the ibm-allMembers operational attribute enumerates the aggregate set of group membership, including static, dynamic, and nested members, as described by the nested group hierarchy. For a given user entry, the ibm-allGroups operational attribute enumerates the aggregate set of groups, including ancestor groups, to which that user has membership.
A requester can only receive a subset of the total data requested, depending on how the ACLs have been set on the data. Anyone can request the ibm-allMembers and ibm-allGroups operational attributes, but the data set returned only contains data for the LDAP entries and attributes that the requester has access rights to. The user requesting the ibm-allMembers or ibm-allGroups attribute must have access to the member or uniquemember attribute values for the group and nested groups in order to see static members, and must be able to perform the searches specified in the memberURL attribute values in order to see dynamic members. For examples:
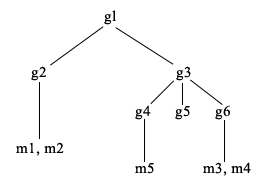
Hierarchy examples

For this example, m1 and m2 are in the member attribute of g2. The ACL for g2 allows user1 to read the member attribute, but user 2 does not have access to the member attribute. The entry LDIF for the g2 entry is as follows:
dn: cn=g2,cn=groups,o=ibm,c=us objectclass: accessGroup cn: g2 member: cn=m1,cn=users,o=ibm,c=us member: cn=m2,cn=users,o=ibm,c=us aclentry: access-id:cn=user1,cn=users,o=ibm,c=us:normal:rsc aclentry: access-id:cn=user2,cn=users,o=ibm,c=us:normal:rsc:at.member:deny:rsc
The g4 entry uses the default aclentry, which allows both user1 and user2 to read its member attribute. The LDIF for the g4 entry is as follows:
dn: cn=g4, cn=groups,o=ibm,c=us objectclass: accessGroup cn: g4 member: cn=m5, cn=users,o=ibm,c=us
The g5 entry is a dynamic group, which gets its two members from the memberURL attribute. The LDIF for the g5 entry is as follows:
dn: cn=g5, cn=groups,o=ibm,c=us objectclass: container objectclass: ibm-dynamicGroup cn: g5 memberURL: ldap:///cn=users,o=ibm,c=us??sub?(|(cn=m3)(cn=m4))
The entries m3 and m4 are members of group g5 because they match the memberURL The ACL for the m3 entry allows both user1 and user2 to search for it. The ACL for the m4 entries doesn't allow user2 to search for it. The LDIF for m4 is as follows:
dn: cn=m4, cn=users,o=ibm,c=us objectclass:person cn: m4 sn: four aclentry: access-id:cn=user1,cn=users,o=ibm,c=us:normal:rsc aclentry: access-id:cn=user2,cn=users,o=ibm,c=us
ldapsearch -D cn=user1,cn=users,o=ibm,c=us -w user1pwd -s base -b cn=g1,
cn=groups,o=ibm,c=us objectclass=* ibm-allmembers
cn=g1,cn=groups,o=ibm,c=us
ibm-allmembers: CN=M1,CN=USERS,O=IBM,C=US
ibm-allmembers: CN=M2,CN=USERS,O=IBM,C=US
ibm-allmembers: CN=M3,CN=USERS,O=IBM,C=US
ibm-allmembers: CN=M4,CN=USERS,O=IBM,C=US
ibm-allmembers: CN=M5,CN=USERS,O=IBM,C=US
ldapsearch -D cn=user2,cn=users,o=ibm,c=us -w user2pwd -s base -b cn=g1,
cn=groups,o=ibm,c=us objectclass=* ibm-allmembers
cn=g1,cn=groups,o=ibm,c=us
ibm-allmembers: CN=M3,CN=USERS,O=IBM,C=US
ibm-allmembers: CN=M5,CN=USERS,O=IBM,C=US
ldapsearch -D cn=user2,cn=users,o=ibm,c=us -w user2pwd -s base -b cn=m3,
cn=users,o=ibm,c=us objectclass=* ibm-allgroups
cn=m3,cn=users,o=ibm,c=us
ibm-allgroups: CN=G1,CN=GROUPS,O=IBM,C=US
ldapsearch -D cn=user2,cn=users,o=ibm,c=us -w user2pwd -s base -b
cn=m1,cn=users,o=ibm,c=us objectclass=* ibm-allgroups
cn=m1,cn=users,o=ibm,c=us