
| 1 | Intermediate representation of the program | Input | Char(*) |
| 2 | Length of intermediate representation of program | Input | Binary(4) |
| 3 | Qualified program name | Input | Char(20) |
| 4 | Program text | Input | Char(50) |
| 5 | Qualified source file name | Input | Char(20) |
| 6 | Source file member information | Input | Char(10) |
| 7 | Source file last changed date and time information | Input | Char(13) |
| 8 | Qualified printer file name | Input | Char(20) |
| 9 | Starting page number | Input | Binary(4) |
| 10 | Public authority | Input | Char(10) |
| 11 | Option template | Input | Char(*) |
| 12 | Number of option template entries | Input | Binary(4) |
| 13 | Error code | I/O | Char(*) |
The Create Program (QPRCRTPG) API converts the symbolic representation of a machine interface (MI) program into an OPM program object. This symbolic representation is known as the intermediate representation of a program.
The QPRCRTPG API creates a program object that resides in the *USER domain and runs in the *USER state. If you want the program object to be temporary, you must do one of the following:
You can specify program objects created with the QPRCRTPG API in CL commands that process objects of type *PGM. For example, you can:
Note: MI instructions that reference system-domain or write-protected objects fail at security levels 40 and 50. At those levels, you must use APIs to work with the objects.
A string containing the intermediate representation of the program to be processed by the QPRCRTPG API. See Program Syntax.
The size, in bytes, of the intermediate representation of the program.
The name and library of the program to be created or replaced. The first 10 characters contain the program name, and the second 10 characters contain the name of the library where the program is located. The special value *CURLIB may be used for the library name.
Text that briefly describes the program.
The name and library containing the source program. The first 10 characters contain the source file name, and the second 10 characters contain the name of the library where the file is located. This places the value in the program object's service description. The special value *NONE may be used for the source file name. If you specify *NONE, no source file information is placed in the program object's service description. A special value, such as *LIBL, is not valid for the source file library.
The file member containing the source program. This places the value in the program object's service description.
This value must be blanks if you specify *NONE as the source file name.
The date and time the member of the source file was last updated. The format of this field is in the CYYMMDDHHMMSS format, where:
| C | Century, where 0 indicates years 19xx and 1 indicates years 20xx. |
| YY | Year |
| MM | Month |
| DD | Day |
| HH | Hour |
| MM | Minute |
| SS | Second |
This places the value in the program object's service description.
This value must be blank if you specify *NONE for the source file name parameter.
The name and library containing the printer file used to generate listings. The first 10 characters contain the printer file name, and the second 10 characters contain the name of the library where the file is located. The only special values supported for the library name are *LIBL and *CURLIB.
This value is ignored if you specify *NOLIST for the generate listing option (see Values for the Option Template Parameter).
The first page number to be used on listings. This value should be between 1 and 9999; otherwise, the API uses 1.
This value is ignored if you specify *NOLIST for the generate listing option (see Values for the Option Template Parameter).
The authority you give the users who do not have specific private authorities to the object, and where the user's group has no specific authority to the object.
The values allowed are:
| *CHANGE |
| *ALL |
| *USE |
| *EXCLUDE |
| The name of an authorization list |
This is an array of options. You can specify between 0 and 17 values. Each entry contains a CHAR(11) value as described in Values for the Option Template Parameter.
The number of option template entries.
The value must be between 0 and 17.
The structure in which to return error information. For the format of the structure, see Error code parameter. If this parameter is omitted, diagnostic and escape messages are issued to the application.
When you are using the QPRCRTPG API, you can specify a value in the option template. Only one value per option should be specified. If you specify more than one, the system only uses the first one. If you specify no value for a given option, the system uses the default value (underlined).
The values allowed are:
| *GEN | Generates a program and places the program in the appropriate library. |
| *NOGEN | No program is generated. The syntax of the intermediate representation of the program is checked, and if the generate listing option is *LIST, a listing is produced. |
The values allowed are:
| *NOREPLACE | Does not replace an existing program by the same name in the specified library. |
| *REPLACE | Replaces the existing program by moving it to the QRPLOBJ library. |
The values allowed are:
| *NOLIST | Does not generate a listing. |
| *LIST | Generates a listing.
You must specify the following parameters:
|
The values allowed are:
| *NOXREF | Does not create cross-reference listing. |
| *XREF | Creates a cross-reference listing of references to variables, labels, or both. |
The values allowed are:
| *NOATR | Does not create a summary listing section. |
| *ATR | Creates a summary listing section. |
| *USER | The user profile of the user running the program is used as a source of authority when this program runs. |
| *ADOPT | When the program runs, the object authority of both the program's owner and user are used. |
| *OWNER | The system uses the user profile of the owner of the program as a source of authority when this program runs. Programs called by this program adopt this authority. |
The values allowed are:
| *ADPAUT | The system uses program-adopted authority from the calling program. |
| *NOADPAUT | The system does not use program-adopted authority from the calling program. |
Note: Authorization to create programs which can adopt authority is controlled by the QUSEADPAUT system value. For more information, refer to the description of this system value in the Work Management topic.
| *SUBSCR | Constrains arrays. This requests additional run-time checks to ensure that references to array elements are not outside the bounds of the declare statement. This option causes the resulting program to run slower. |
| *NOSUBSCR | Does not constrain arrays. The results of references to array elements outside the bounds of the declare statement are not defined. |
| *UNCON | Allows fully unconstrained arrays. This ensures that references to array elements outside the bounds of the declare statement act as if the array element actually exists. |
Note: This program attribute may be changed at run-time using the Override Program Attributes (OVRPGATR) MI instruction.
| *SUBSTR | Constrains strings. This requests additional run-time checks to ensure that references to character strings are not outside the bounds of the declare statement. This option causes the resulting program to run slower. |
| *NOSUBSTR | Does not constrain strings. The results of substring references outside the bounds of the declare statement are not defined. |
Note: You can change this program attribute at run-time using the Override Program Attributes (OVRPGATR) MI instruction.
The values allowed are:
| *CLRPSSA | Initializes static storage. This code clears the program static storage area (PSSA) on entry using the Call External (CALLX) MI instruction. |
| *NOCLRPSSA | Does not initialize the PSSA. |
The values allowed are:
| *CLRPASA | Initializes automatic storage. This code clears the program automatic storage area (PASA) on entry using the Call External (CALLX) MI instruction. |
| *NOCLRPASA | Does not initialize the PASA. |
The values allowed are:
| *NOIGNDEC | Does not ignore decimal data errors.
When you specify *NOIGNDEC, decimal values used in numeric operations are checked for valid decimal digits and sign codes. If the system finds an error, it signals an exception. |
| *IGNDEC | Ignores data decimal errors.
When you specify *IGNDEC, decimal values used in numeric operations ensure they contain valid decimal digit and sign codes. However, the system treats digits that are not valid as zeros and signs that are not valid as positive signs. There is no exception signaled. |
This option applies to only a subset of the numeric operations you specify.
Note: In all cases, the system signals decimal data errors if you use data pointers to address any of the instruction's operands.
The following list contains the MI instructions this option affects:
| MI Instruction | Packed Source Operands Supported | Zoned Source Operands Supported | Notes |
|---|---|---|---|
| ADDN | X | ||
| CMPNV | X | ||
| CVTCN | X | X | You must specify operand 3 (the numeric view to be used for operand 2) as a constant and no data-pointer-defined operands. |
| CVTDFFP | X | ||
| CVTNC | X | X | You must specify operand 3 (the numeric view to be used for operand 1) as a constant and no data-pointer-defined operands. |
| CPYNV | X | X | You must specify no data-pointer-defined operands. |
| DIV | X | ||
| DIVREM | X | ||
| EDIT | X | You must specify no data-pointer-defined operands. | |
| EXTRMAG | X | ||
| MULT | X | ||
| NEG | X | ||
| REM | X | ||
| SCALE | X | ||
| SUBN | X |
When you specify *IGNDEC, the system may still signal the decimal data exception. That is, other MI instructions and instruction combinations not listed above may signal the decimal data exception when the system finds decimal data that is bad.
| *NOIGNBIN | The system handles binary data size errors normally. When a binary size error occurs, an exception is signaled and the receiver contains the left-truncated result. |
| *IGNBIN | The system ignores binary data size errors. This is used when an overflow or underflow occurs on a computation and when a control MI instruction has a receiver that is a binary field. The receiver contains the left-truncated result. |
The values allowed are:
| *NOOVERLAP | Does not support coincident operands. If you specify *NOOVERLAP, you guarantee that coincident operand overlap will not occur while running the instruction. Therefore, the system can use the receiver on an instruction as a work area during operations performed to produce the final result. Using the receiver as a work area does not use as much processor resource as would be required to move the final result from an internal work area to the receiver. |
| *OVERLAP | Supports coincident operands. If you specify *OVERLAP, the operands on an MI instruction may overlap. Therefore, the system cannot use the receiver on an instruction as a work area during operations that produce the final result. This can require more processor resource for running the instruction but it ensures valid results if an overlap occurs. |
The following is a list of instructions this option affects:
| *NODUP | This does not allow a program object to be declared more than once. This requests that duplicate declare (DCL) statements be diagnosed as errors. |
| *DUP | This allows a program object to be declared more than once. This requests that program objects declared more than once be pooled and not be diagnosed as errors. |
| *OPT | This optimizes the program. In most instances, this produces the smallest and best running program. Occasionally, the source program may signal a MCH2802 escape message during processing. If this occurs, you should not optimize the program. |
| *NOOPT | This does not optimize the program. This requests the normal level code optimization when you create the program. |
The values allowed are:
| *CURRENT | The object is to be used on the release of the operating system currently running on your system. |
| *PRV | The object is to be used on the previous release with modification level 0 of the operating system. |
| target-release | Specify the release in the format VxRxMx. |
| Message ID | Error Message Text |
|---|---|
| CPD0078 D | Value &3 for parameter not a valid name. |
| CPF2143 E | Cannot allocate object &1 in &2 type *&3. |
| CPF2144 E | Not authorized to &1 in &2 type *&3. |
| CPF2146 E | Owner of object &1 and object being replaced not the same. |
| CPF2283 E | Authorization list &1 does not exist. |
| CPF223B D | &1 in &2 type *&3 adopted authority from previous call levels was set to *NO. |
| CPF223E E | Authority check for use adopted authority attribute failed. |
| CPF3CF1 E | Error code parameter not valid. |
| CPF3C35 E | Value &3 for parameter &2 not a valid name. |
| CPF3C5A E | Number of option template entries is not valid. |
| CPF3C5B E | Option template entry is not valid. |
| CPF3C5C E | Source file name and library is not valid. |
| CPF3C5D E | Source file member is not valid. |
| CPF3C5F E | Internal Representation of Program (IRP) string length parameter is not valid. |
| CPF3C50 E | Program &1 not created. |
| CPD0078 D | Value &3 for parameter not a valid name. |
| CPD3C50 D | Value &1 for the IRG string length parameter was not valid. |
| CPD3C52 D | Number of option template entries is not valid. |
| CPD3C53 D | Option template entry is not valid. |
| CPD3C54 D | Source file name and library is not valid. |
| CPD3C55 D | Source file member is not valid. |
| CPD3C56 D | Source file last changed date and time is not valid. |
| CPF3C56 E | Source file last changed date and time is not valid. |
| CPF3C60 E | Program name and library is not valid. |
| CPF3C61 E | Authority is not valid. |
| CPF3C62 E | Source file library specified. |
| CPF3C63 E | Source file member specified. |
| CPF3C64 E | Source file last changed date and time specified. |
| CPF3C90 E | Literal value cannot be changed. |
| CPF6301 E | Intermediate representation of program (IRP) contains &1 errors. Probable compiler error. |
| CPF6303 E | Message &1, &2 received while running create program command. |
| CPF6304 E | Library &1 not found. |
| CPF6306 E | Program &1 in library &2 already exists. |
| CPF6307 E | Program template value at offset &1, bit &2, length &3 not valid. |
| CPF6308 E | Not authorized to create program. |
| CPF6309 E | Not authorized to library &1. |
| CPF6455 E | Member &2 file &1 in library &3 not found. |
| CPF6457 E | Cannot allocate library &1 for program insertion. |
| CPF6551 E | Work space &2 cannot be extended. Probable compiler error. |
| CPF6552 E | Space &2 type &3 subtype &4 not PRM workspace. |
| CPF6553 E | PRM permanent table resolution failed. Probable compiler error. |
| CPF6554 E | Type of IST object &4 at offset &3 not valid. Probable PRM error. |
| CPF6555 E | Addressability field type not valid for IST number &4 at offset &3. Probable PRM error. |
| CPF6557 E | Error condition for IST &4 at &3 of IST space not valid. Probable PRM error. |
| CPF6560 E | Operation code &5 in MI instruction &3 at offset &6 not found in QPRODT. |
| CPF6561 E | Operand &4 in &3 at offset &5 in program template not valid. |
| CPF6563 E | Program was too large to be created. |
| CPF6564 E | Machine storage limit violation. |
| CPF6565 E | User profile storage limit exceeded. |
| CPF9872 E | Program or service program &1 in library &2 ended. Reason code &3. |
The QPRCRTPG API creates programs that have the following attributes:
A program object consists of an instruction stream and an object definition table (ODT). The intermediate representation of a program defines both of these components. It consists of one or more statements:

Instruction statements define MI instructions placed in the instruction stream. Declare statements define program objects placed in the ODT. Directive statements:
The following sections explain how to define these statements.
Note: In the diagrams below, names that begin with an uppercase letter identify values specified in another diagram. Names that begin with a lowercase letter identify values defined in the table below the diagram.
The following diagram and table show the possible labels:
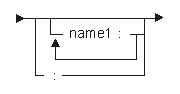
Each name specified in the label generates a branch-point program object corresponding to the next MI instruction.
| Constant | Range | Description |
|---|---|---|
| name1 | Any | Label name for next instruction |
Declare statements define program data objects. All the declare statements in a program build the object definition table (ODT).
You cannot specifically declare branch and entry-point program objects. However, you can declare branch-point program objects using labels. You can also declare entry-point program objects using the entry directive statement.
The types of declare statements follow:
The following diagram and table show the scalar-data-object declare statement:
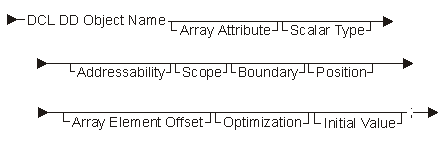
Only certain combinations of attributes are allowed based on the data object's addressability. The table below shows these combinations.
| Address-ability | Array Attribute | Array Element Offset | Position | Boundary | Initial Value |
|---|---|---|---|---|---|
| STAT | X | X | X | ||
| X | X | X | |||
| AUTO | X | X | X | ||
| X | X | X | |||
| DEF | X | X | X | X | |
| X | X | X | X | ||
| DIR | X | X | X | X | |
| X | X | X | X | ||
| BAS | X | X | X | ||
| BASPCO | X | X | X | ||
| PARM | X | X |
The following diagram and table show the possible object names:
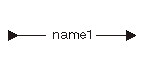
| Constant | Range | Description |
|---|---|---|
| name1 | Any | Program object name to be declared |
The following diagram and table show the possible array attributes:
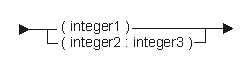
| Constant | Range | Description |
|---|---|---|
| integer1 | 1 to 16 776 191 | Dimension of the data object with an implied lower bound of 1. |
| integer2 | -2 147 483 648 to 2 147 483 647 | Lower bound of the array. |
| integer3 | integer2 to 2 147 483 647 | Upper bound of the array. The dimension (integer3 - integer2) cannot exceed 16 776 191. |
See Code disclaimer information for information pertaining to code examples.
The following declare statements each define an array of 50 elements. The elements of ARRAY1 are numbered 1 to 50. The elements of ARRAY2 are numbered 0 to 49. Each element of the array is a BIN(2) field. The addressability of the arrays is static.
DCL DD ARRAY1(50) BIN(2); DCL DD ARRAY2(0:49) BIN(2);
The following diagram and tables show the possible data types of scalar items:
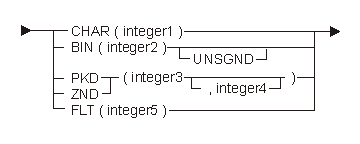
If you specify no value, the system uses BIN(2).
| Keyword | Description |
|---|---|
| CHAR | Scalar type is a character string. |
| BIN | Scalar type is binary. |
| UNSGND | Scalar type is unsigned binary. If you do not specify this value, the scalar type is signed binary. |
| PKD | Scalar type is packed decimal. |
| ZND | Scalar type is zoned decimal. |
| FLT | Scalar type is floating-point. |
| Constant | Range | Description |
|---|---|---|
| integer1 | See description. | Length in bytes of the character data object. If the data object is an array, the range is 1 to 32 767. Otherwise, the range is 1 to 16 776 191. |
| integer2 | 2 or 4 | Length in bytes of the binary data object. |
| integer3 | 1 to 31 | Total digits in the data object. |
| integer4 | 0 to integer3 | Number of digits to the right of the assumed decimal point in the data object. |
| integer5 | 4 or 8 | Precision in bytes of the data object. |
The following diagram and tables show the possible addressabilities:
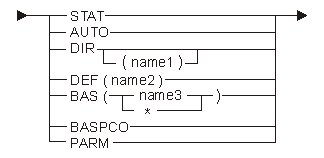
| Keyword | Description |
|---|---|
| STAT | Addressability type is direct static. |
| AUTO | Addressability type is direct automatic. |
| DIR | Addressability type is defined. See Using Space Objects for more information. |
| DEF | Addressability type is direct on the previous space. |
| BAS | Addressability type is based. |
| * | Object does not have explicit basing object. |
| BASPCO | Addressability type is based on process communication object space pointer. |
| PARM | Addressability type is a parameter. |
| Constant | Range | Description |
|---|---|---|
| name1 | Any | Space object name |
| name2 | Any | Scalar data object name or pointer data object name |
| name3 | Any | Pointer data object name or space pointer object name |
If you specify no value, the system uses STAT.
Scope refers to the ability to export a variable so that other programs can access it. The following diagram and table show the possible scopes:
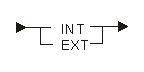
| Keyword | Description |
|---|---|
| INT | Data object is not externally accessible |
| EXT | Data object is externally accessible |
If you specify no value, the system uses INT.
The following diagram and table show the possible boundaries:

| Constant | Range | Description |
|---|---|---|
| integer1 | 1, 2, 4, 8, 16 | Data object boundary |
The following diagram and table show the possible positions:
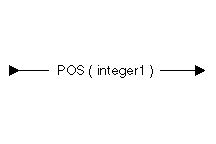
| Constant | Range | Description |
|---|---|---|
| integer1 | 1 to 16 776 191 | Data object position |
The following declare statements show how POS can be used along with DEF to access the same storage space in different ways:
DCL DD DATETIME CHAR(12); DCL DD DATE CHAR(6) DEF(DATETIME); DCL DD TIME CHAR(6) DEF(DATETIME) POS(7);
DATETIME represents a 12 character time and date stamp. The first 6 characters contain the date and the second 6 characters contain the time.
The following diagram and table show the possible array element offsets:
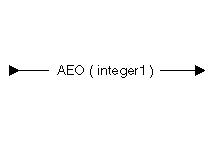
| Constant | Range | Description |
|---|---|---|
| integer1 | 1 to 32767 | Array element offset |
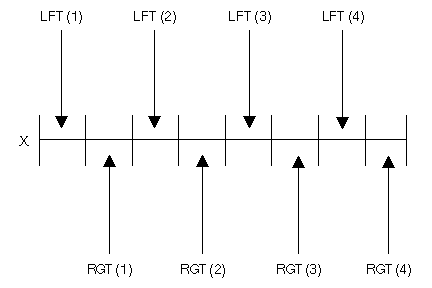
The following example shows AEO used in conjunction with DEF and POS:
DCL DD X CHAR(16); DCL DD LFT(4) BIN(2) DEF(X) AEO(4) POS(1); DCL DD RGT(4) BIN(2) DEF(X) AEO(4) POS(3);
Both LFT and RGT redefine the storage declared by X. Because the size of each array element is smaller than the array element offset, there are 2-byte gaps between each array element:
Optimization determines whether or not an item can be moved to a register and stored there over time. The following diagram shows the possible optimization:
This value indicates that the data object contains an abnormal value. You cannot optimize the value for more than a single reference because the value may be changed in a manner that the QPRCRTPG API cannot detect.
The following diagram and table show each possible initial value:
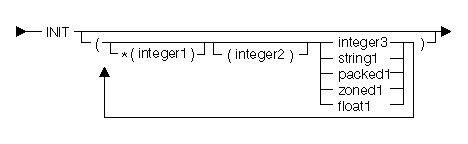
| Constant | Range | Description |
|---|---|---|
| integer1 | 1 to 16 776 191 | Position of elements in a character string |
| integer1 | -2 147 483 648 to 2 147 483 647 | Position of elements in an array |
| integer2 | 1 to 16 776 191 | Replication factor in a character string or array |
| integer3 | Any | Initial value for signed and unsigned binary data objects |
| string1 | Any | Initial value for character string data objects |
| packed1 | Any | Initial value for packed decimal data objects |
| zoned1 | Any | Initial value for zoned decimal data objects |
| float1 | Any | Initial value for floating-point data objects |
The following declare statement declares and initializes a 10-element array:
DCL DD IV(10) BIN(2) STAT INIT((1)10,*(2)(2)11,*(4)(3)12,*(7)(4)13);
There are four initial value elements. The following table describes this function:
| Initial Value Element | Result | Position | Replication Factor | Initial value |
|---|---|---|---|---|
| (1)10 | IV(1)=10 | 1 (default) | 1 | 10 |
| *(2)(2)11 |
IV(2)=11 IV(3)=11 |
2 | 2 | 11 |
| *(4)(3)12 |
IV(4)=12 IV(5)=12 IV(6)=12 |
4 | 3 | 12 |
| *(7)(4)13 |
IV(7)=13 IV(8)=13 IV(9)=13 IV(10)=13 |
7 | 4 | 13 |
The following diagram and table show the pointer-data-object declare statement:
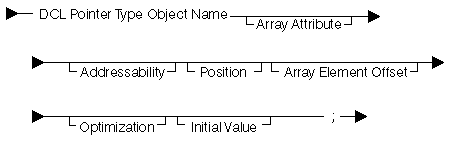
The system only allows certain combinations of attributes based on the data object's addressability. These combinations are listed as follows:
| Address-ability | Array Attribute | Array Element Offset Attribute | Position Attribute | Initial Value Attribute |
|---|---|---|---|---|
| STAT | X | X | X | |
| AUTO | X | X | X | |
| DEF | X | X | X | |
| X | X | |||
| DIR | X | X | X | |
| X | X | |||
| BAS | X | X | ||
| BASPCO | X | X | ||
| PARM | X |
The following diagram and table show the possible pointer types:
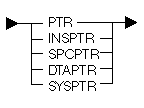
| Keyword | Description |
|---|---|
| PTR | Pointer type is not specified. |
| INSPTR | Pointer type is the instruction pointer. |
| SPCPTR | Pointer type is the space pointer. |
| DTAPTR | Pointer type is the data pointer. |
| SYSPTR | Pointer type is the system pointer. |
If you specify an initial value, you must specify INSPTR, SPCPTR, DTAPTR or SYSPTR.
The following diagram and table show the possible array attributes:
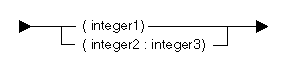
| Constant | Range | Description |
|---|---|---|
| integer1 | 1 to 1 000 000 | Dimension of the data object with an implied lower bound of 1. |
| integer2 | -2 147 483 648 to 2 147 483 647 | Lower bound of the array. |
| integer3 | integer2 to 2 147 483 647 | Upper bound of the array. The dimension (integer3 - integer2) should not exceed 1 000 000. |
The following diagram and tables show the possible addressabilities:
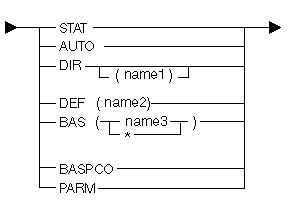
| Keyword | Description |
|---|---|
| STAT | Addressability type is direct static. |
| AUTO | Addressability type is direct automatic. |
| DIR | Addressability type is defined. See Using Space Objects for more information. |
| DEF | Addressability type is defined. |
| BAS | Addressability type is based. |
| * | Object does not have explicit basing object. |
| BASPCO | Addressability type is based on the process communication object space pointer. |
| PARM | Addressability type is parameter. |
| Constant | Range | Description |
|---|---|---|
| name1 | Any | Space object name |
| name2 | Any | Scalar data object name or the pointer data object name |
| name3 | Any | Pointer data object name or the space pointer machine object name |
The following diagram and table show the possible positions:
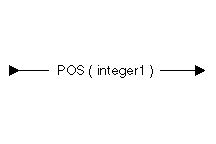
| Constant | Range | Description |
|---|---|---|
| integer1 | 1 to 16 776 191 | Data object position |
The following diagram and table show the possible array element offset values:
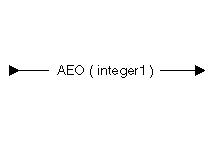
| Constant | Range | Description |
|---|---|---|
| integer1 | 1 to 32 767 | Array element offset |
The following diagram shows the possible optimizations:
This value indicates that the data object contains an abnormal value. The system cannot optimize a value for more than a single reference because the value may be changed in a manner the QPRCRTPG API cannot find.
The following diagram shows each possible initial value:

An initial value can only be specified if a pointer-type value other than PTR is specified. The syntax of the initial value is based on the pointer-type value that was used.
The following diagram and table show the possible initial value for the instruction pointer:
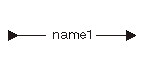
| Constant | Range | Description |
|---|---|---|
| name1 | Any | Label name |
The following statement declares and initializes an instruction pointer:
LABELI: : : DCL INSPTR INSTRUCTION_PTR INIT(LABELI);
The following diagram and table show the initial value for the space pointer:
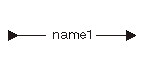
| Constant | Range | Description |
|---|---|---|
| name1 | Any | Scalar data object name or pointer data object name |
The following statement declares and initializes a space pointer:
DCL PTR ANY_POINTER; DCL SPCPTR SPACE_PTR INIT(ANY_POINTER);
The pointer SPACE_PTR is initialized to point to the space location containing ANY_POINTER. It does not contain the value of ANY_POINTER.
The following diagram and table show the initial value for the data pointer:
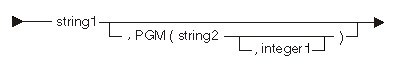
| Constant | Range | Description |
|---|---|---|
| string1 | 32 bytes | External data object name |
| string2 | 30 bytes | Program containing external data object |
| integer1 | 0 to 255 | Subtype of program |
The following statement declares and initializes a data pointer:
DCL DTAPTR DVALUE INIT("DBINARY",PGM("DPGM"));
The pointer DTAPTR refers to the externally defined program object DBINARY contained in program DPGM.
The following diagram and tables show the initial value for the system pointer:
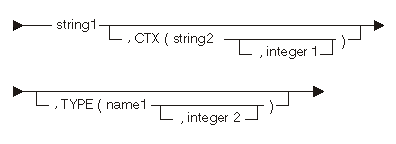
| Constant | Range | Description |
|---|---|---|
| string1 | 1 to 30 bytes | System object |
| string2 | 1 to 30 bytes | Context where the system object is located |
| integer1 | 0 to 255 | Subtype of the context |
| name1 | See table below. | Symbolic type of the system object |
| integer2 | 0 to 255 | Subtype of the system object |
The following system object types are supported:
| Type | Description |
|---|---|
| PGM | Program |
| CTX | Context |
| Q | Queue |
| SPC | Space |
| PCS | Process control space |
The following statement declares and initializes a system pointer:
DCL SYSPTR SYSTEM_PTR INIT("MYPGM",CTX("PGMLIB"),TYPE(PGM));
The pointer SYSTEM_PTR refers to the *PGM object MYPGM in the PGMLIB library.
The following diagram and table show the space-pointer-machine-object declare statement:
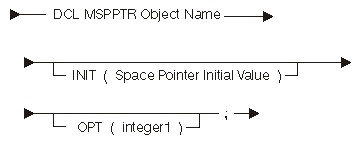
| Constant | Range | Description |
|---|---|---|
| integer1 | 0 to 255 | Optimization priority value, where 255 is the highest priority |
The iSeries system provides two types of pointers that can access data:
The MSPPTR has the following restrictions:
Because the MSPPTR has the above restrictions, the translator often assigns the MSPPTR to a hardware register for the life of the entire program unit. What this means is that loads may be eliminated from the generated code.
The following diagram and tables show the operand-list declare statement:
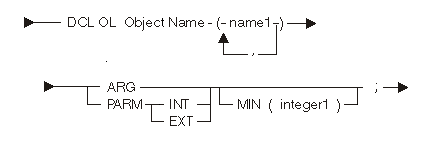
| Keyword | Description |
|---|---|
| ARG | Defines the argument list |
| PARM | Defines the parameter list |
| INT | An internal parameter list |
| EXT | An external parameter list |
| Constant | Range | Description |
|---|---|---|
| name1 | Any | Scalar data object or a pointer data object name. Up to 255 names can be specified. |
| integer1 | 0 to 255 | Minimum number of elements that the list can contain. This implicitly defines a variable-length operand list. If you do not specify the operand list, the system defines a fixed-length operand list. Up to 255 names can be specified. |
The following statements declare both argument and parameter operand lists along with the associated argument and parameter data objects:
DCL DD ARG1 BIN(2); DCL DD ARG2 CHAR(3); DCL OL ARGUMENT_LIST (ARG1, ARG2) ARG; DCL DD PARM1 BIN(2) PARM; DCL DD PARM2 CHAR(3) PARM; DCL OL PARAMETER_LIST (PARM1, PARM2) PARM EXT;
A parameter operand list that refers to the data objects has parameter (PARM) addressability.
The following diagram and table show the instruction-definition-list declare statement:

| Constant | Range | Description |
|---|---|---|
| name1 | Any | Label name. Up to 255 names can be specified. |
The following statements declare and use an instruction definition list:
LABEL1: : : DCL IDL INSTRUCTION_LIST (LABEL1,LABEL2,LABEL3); : : LABEL2: B INSTRUCTION_LIST(3); /* Branch to LABEL3 */ : : LABEL3:
The following diagram and tables show the exception-description declare statement:
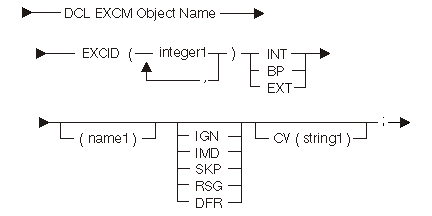
| Keyword | Description |
|---|---|
| INT | Exception handler type is the internal entry point. |
| BP | Exception handler type is the internal branch point. |
| EXT | Exception handler type is the external entry point. |
| IGN | Exception handling action ignores any exceptions and continues processing. |
| IMD | Exception handling action passes control to the specified exception handler. This is the default. |
| SKP | Exception handling action is to continue to search for another exception description to handle the exception. |
| RSG | Exception handling action continues to search for an exception description by signaling the exception again to the previous call. |
| DFR | Exception handling action postpones handling and saves exception data for later exception handling. |
| Constant | Range | Description |
|---|---|---|
| integer1 | 0 to 65535 | Exception identifier |
| name1 | Any | Name of the label for branch point exception handlers, name of the entry point for the internal exception handlers, and the name of the system pointer for the external exception handlers |
| string1 | 1 to 32 bytes | Compare value |
The following diagram and tables show the space-object declare statement:
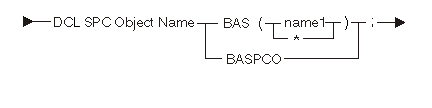
| Keyword | Description |
|---|---|
| BAS | Addressability type is based. |
| * | Object does not have explicit basing object. |
| BASPCO | Addressability type is based on process communication object space pointer. |
| Constant | Range | Description |
|---|---|---|
| name1 | Any | Basing pointer name for the space |
For information on using space objects, refer to Using Space Objects.
The following diagram and tables show the constant-object declare statement:
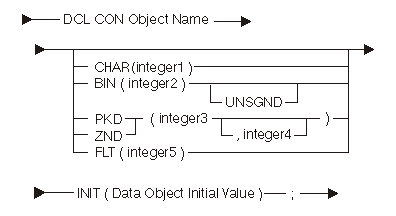
| Keyword | Description |
|---|---|
| CHAR | Scalar type is character string. |
| BIN | Scalar type is binary. |
| UNSGND | Scalar type is unsigned binary. |
| PKD | Scalar type is packed decimal. |
| ZND | Scalar type is zoned decimal. |
| FLT | Scalar type is floating-point. |
| Constant | Range | Description |
|---|---|---|
| integer1 | 1 to 32 767 | Length in bytes of the character data object |
| integer2 | 2 or 4 | Length in bytes of the binary data object |
| integer3 | 1 to 31 | Number of decimal digits |
| integer4 | 0 to integer3 | Number of fractional digits |
| integer5 | 4 or 8 | Number of bytes in floating-point constant |
If you do not specify a scalar type, the system uses BIN(2).
An instruction statement defines an MI instruction. The instruction stream used to create the program is made up of all the instruction statements in the intermediate representation of the program.
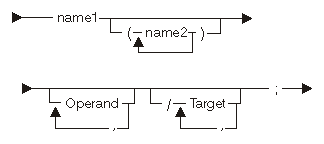
| Constant | Range | Description | ||||||||
|---|---|---|---|---|---|---|---|---|---|---|
| name1 | See description. | Opcode for this instruction, as defined in the iSeries Machine Interface Instructions . | ||||||||
| name2 | S, R, B, I | This is the form of the instruction.
|
For the semantic meanings and the syntax restrictions (number and types of operands, optional forms, and so on) for individual MI instructions, see the iSeries Machine Interface Instructions.
Following the abbreviated instruction name, you can specify the optional forms of certain MI instructions using a string of characters enclosed in parentheses. The following is an example of some of the various combinations possible for a single MI instruction, ADD NUMERIC:
ADDN A,B,C; Add numeric (A=B+C)
ADDN(S) A,B; Add numeric short (A=A+B)
ADDN(SR) A,B; Add numeric short and round (A=A+B)
ADDN(SB) A,B/POS(X),NEG(Y); Add numeric short and branch (A=A+B,
branch to X if A>0, branch to Y if A<0)
ADDN(RI) A,B,C/POS(I),NEG(J); Add numeric round and indicator (A=B+C;
I='on' if A>0; j='on' if A<0 )
Also note that the order of characters in the optional form string is not significant. Thus, all of the following instructions are both valid and equivalent:
ADDN(SRB)A,B/POS(X); Add numeric short, round and branch ADDN(SBR)A,B/POS(X); Add numeric short, round and branch ADDN(RSB)A,B/POS(X); Add numeric short, round and branch
The following diagram and table show the possible operands:
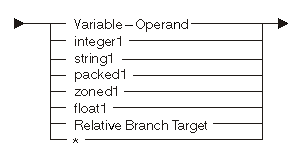
| Constant | Range | Description |
|---|---|---|
| integer1 | Any | Numeric binary scalar operand |
| string1 | Any | Character scalar operand |
| packed1 | Any | Numeric packed decimal scalar operand |
| zoned1 | Any | Numeric zoned decimal scalar operand |
| float1 | Any | Numeric floating-point scalar operand (4 or 8 bytes) |
| * | Null operand |
The following diagram and table show the possible variable operands:
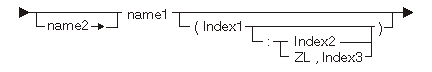
| Constant | Range | Description |
|---|---|---|
| name1 | Any | Data object name to be used as a primary operand. |
| name2 | Any | Pointer data object to be used as the basing pointer. |
| Index1 | See description. | Subscript or substring start position. The range for array subscripts is between the lower bound of the array and the upper bound of the array. The range for substrings is between 1 and 16 776 191. |
| Index2 | 1 to 32 767 | Length of the substring. |
| Index3 | 0 to 32 767 | Length of the substring (zero allowed). |
The following diagram and table show the possible relative branch targets:
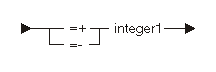
| Constant | Range | Description |
|---|---|---|
| integer1 | 1 to 4095 | Branch target instruction number relative to the current instruction. You must label the target (named or null label). |
Note: You cannot use blanks between either the '
=+
' symbol set and integer1 or the '
=-
' symbol set and integer1. However, a blank must precede the symbol sets.
The following instructions illustrate the use of relative branch targets:
CPYNV X,0; CMPBLA(B) A,'1'/EQ( =+2); CPYNV X,1; : CPYNV Y,X; /* Destination of relative branch */
Note: A null label is placed in the destination instruction of the relative branch.
The following diagram and table show the possible targets:
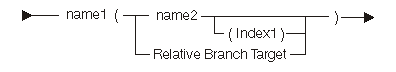
| Constant | Range | Description |
|---|---|---|
| name1 | See keyword table. | Keyword for branch or indicator forms. You can use an N before keywords to negate the condition except for IGN and DFR. See "Resultant Conditions", under each MI instruction for the valid values. |
| name2 | Any | Label name, instruction pointer name, or instruction definition list name for the branch form. The name of character variable is for the indicator form. |
| Index1 | 1 to 255 | Instruction definition list index. You can only specify this value when name2 is the name of an instruction definition list. |
The following table shows the branch and indicator keywords:
| Keyword | Description |
|---|---|
| Group 1 | |
| HI MXD NOR POS TR ZC | High Mixed Normalized Positive Truncated record Zero and carry |
| Group 2 | |
| CR DEN IGN LO NEG NTZNTC RO | Complete record Denormalized Exception ignored Low Negative Not-zero and no carry Receiver overrun |
| Group 3 | |
| AUTH DFR DQ EQ INF SE SGN ZER ZNTC | Authorized Exception postponed Dequeued Equal Infinity Source all used Signaled Zero Zero and no carry |
| Group 4 | |
| EC NAN NTZC UNEQ UNOR | Escape code encountered Not a number (NaN) Not-zero and carry Unequal Unordered |
By adding N to the beginning of the appropriate keyword you can form a not condition. For example, the code for "not equal" is NEQ.
All conditions coded on a particular instruction must be mutually exclusive. All conditions within a group are equivalent, and therefore, only one may be specified. For example, POS (positive) and HI (high) cannot be coded on the same instruction.
The not form of a condition is satisfied by any condition from another group. For example, NEQ (not equal) is satisfied by HI (high), LO (low), or UNOR (unordered). Therefore, you cannot specify NEQ with any of the other three. However, you can use NEQ and EQ (or any other keyword in group 3) together because they are mutually exclusive.
The following diagram and table show the possible indexes:
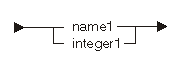
| Constant | Range | Description |
|---|---|---|
| name1 | See description below. | Binary variable to use as the index |
| integer1 | See description below. | Integer value to use as the index |
An index is a numeric value that qualifies an array or substring reference. The context in which the index is used determines the range. For more information, refer to the preceding tables.
The directive statements are as follows:
The title directive statement causes a heading to appear on the listings. Only one title directive statement may be specified in a program. The following diagram and table show the title directive statement:
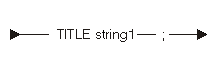
| Constant | Range | Description |
|---|---|---|
| string1 | Any | Text of the title |
The space directive statement causes a blank line to appear in the listing. The following diagram and table show the space directive statement:
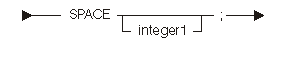
| Constant | Range | Description |
|---|---|---|
| integer1 | Any | Number of lines to skip |
The eject directive statement causes the next line to appear on a new page. The following diagram shows the eject directive statement:
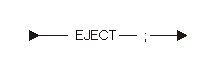
The break directive statement allows symbolic breakpoints to be defined. The following diagram and table show the break directive statement:
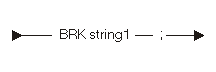
| Constant | Range | Description |
|---|---|---|
| string1 | Any | Breakpoint name |
The following diagram and tables show the entry directive statement:
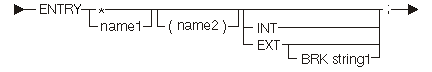
| Keyword | Description |
|---|---|
| INT | Internal entry point. |
| EXT | External entry point. |
| BRK | Symbolic breakpoint is associated with the entry point. |
| * | Entry point defined has no name or is associated with the next MI instruction. |
| Constant | Range | Description |
|---|---|---|
| name1 | Any | Entry point name being defined |
| name2 | Any | Parameter list name for this entry point |
| string1 | 1-10 bytes | Breakpoint name |
The default scope is internal (INT).
The entry statement defines entry point program objects. The next instruction number is associated with this entry point. The entry statement is to be the definition point for this object, so the ODT number assigned to this object is the next available ODT number.
The following diagram shows the reset directive statement:

The specified name is a previously declared space object. The reset statement causes subsequent data object declarations containing the DIR attribute to use the specified space object. The system maintains next byte counts for each space object; these counts are not affected by the reset statement. For more information, see Using Space Objects.
The following diagram shows the program end directive statement:
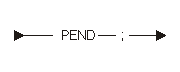
This must be the last statement in the program. To ensure comments and strings end before processing the PEND statement, use the following statement:
/*'/*'/*"/*"*/; PEND;;;
This section contains additional information for coding the intermediate representation of a program.
Use the following guidelines when using declare statements:
Example: The following sets of declare statements are valid:
DCL DD A CHAR(5); DCL DD B CHAR(1) DEF(A); DCL DD A CHAR(5); DCL DD X BIN(2); DCL PTR P1 AUTO; DCL DD B CHAR(1) DEF(A);
Example: The following declare statements are not valid because B is defined on A but is declared before A:
DCL DD B CHAR(1) DEF(A); DCL DD A CHAR(5);
This restriction also applies when there is a chain of dependencies.
Example: In the figure below, B is defined on A and C is defined on B:
DCL DD A CHAR(5); DCL DD B CHAR(3) DEF(A); DCL DD C CHAR(1) DEF(B);
If any object in a chain of definitions, as shown in the previous examples, has an initial value specified, then the following restrictions apply:
Example: The following declare statements are valid because:
DCL DD A CHAR(5); DCL DD B CHAR(3) DEF(A) INIT(C'YES'); DCL DD C CHAR(1) DEF(B);
Space objects, when used in conjunction with program objects declared with the DIR attribute, provide a convenient way of declaring structures.
Note: Space objects, as used here, do not refer to i5/OS space objects.
When you declare a space object, a scalar data object with a scalar type of CHAR(32767) is created. This object contains the structure to be defined. Associated with this object is a "next byte" count. This value is initially 1 and represents the position where the next structure element will be placed.
After you declare a space object, you can declare one or more scalar or pointer data objects with an addressability attribute of DIR. As a result, the system automatically declares each object with the DEF and POS attributes. The name associated with the DEF attribute is the most recently declared space object. The value associated with the POS attribute is the space object's next byte count. After you declare the object, the system sets the next byte count associated with the space object to the next available position within the structure.
The group of declare statements on the left is equivalent to the group on the right:
DCL SPC X BAS(PTR); DCL DD X CHAR(32767) BAS(PTR); DCL DD A CHAR(2) DIR; DCL DD A CHAR(2) DEF(X) POS(1); DCL DD B ZND(5,2) DIR; DCL DD B ZND(5,2) DEF(X) POS(3); DCL DD C FLT(4) DIR; DCL DD C FLT(4) DEF(X) POS(8);
Data objects declared with DIR may also have an explicit POS value. The object is defined on the appropriate space object and uses the specified POS value. However, the next byte count is changed only if the POS value causes the count to increase.
The group of declare statements on the left is equivalent to the group on the right:
DCL SPC X BAS(PTR); DCL DD X CHAR(32767) BAS(PTR); DCL DD A CHAR(4) DIR; DCL DD A CHAR(4) DEF(X) POS(1); DCL DD B CHAR(4) POS(20) DIR; DCL DD B CHAR(4) DEF(X) POS(20); DCL DD C CHAR(4) DIR; DCL DD C CHAR(4) DEF(X) POS(24); DCL DD D CHAR(4) POS(10) DIR; DCL DD D CHAR(4) DEF(X) POS(10); DCL DD E CHAR(4) DIR; DCL DD E CHAR(4) DEF(X) POS(28);
When you declare objects with an explicit boundary other than 1, the object is positioned on the next available byte with that boundary. The position of any data object with the direct attribute is the next available byte in the space if no boundary or position is specified. The position of any pointer object with the direct attribute is the next available byte in the space if no position is specified. Space objects are assumed to begin on a 16-byte boundary. You must ensure this condition exists at run-time.
The group of declare statements on the left is equivalent to the group on the right:
DCL SPC X BAS(PTR); DCL DD X CHAR(32767) BAS(PTR); DCL DD A CHAR(1) DIR; DCL DD A CHAR(1) DEF(X) POS(1); DCL DD B FLT(4) DIR; BDRY(4); DCL DD B FLT(4) DEF(X) POS(5); DCL PTR C DIR; POS(17); DCL PTR C DEF(X) POS(17);
You can use the reset directive statement to change the name of the space object to be used by subsequent declare statements.
The group of declare statements on the left is equivalent to the group on the right:
DCL SPCPTR PTR1; DCL SPCPTR PTR1; DCL SPCPTR PTR2; DCL SPCPTR PTR2; DCL SPC X BAS(PTR1); DCL DD X CHAR(32767) BAS(PTR1); DCL DD A CHAR(2) DIR; DCL DD A CHAR(2) DEF(X) POS(1); DCL DD B ZND(5,2) DIR; DCL DD B ZND(5,2) DEF(X) POS(3); DCL SPC Y BAS(PTR2); DCL DD Y CHAR(32767) BAS(PTR2); DCL DD C CHAR(5) DIR; DCL DD C CHAR(5) DEF(Y) POS(1); DCL DD D CHAR(7) DIR; DCL DD D CHAR(7) DEF(Y) POS(6); RESET X; DCL DD E CHAR(3) DIR; DCL DD E CHAR(3) DEF(X) POS(8);
This section describes the syntax of constant values.
Integers define signed and unsigned binary scalar data values. The two forms of integers are decimal and hexadecimal. The decimal form is a sequence of digits optionally preceded by a sign. The hexadecimal form is a string of hexadecimal digits delimited with apostrophes and preceded by an H. Neither form may exceed the 4-byte limit on binary numbers. When the value of the integer is between -4095 and +8191, the QPRCRTPG API converts the integer to an immediate operand where it can.
+123 -1 54788 H'0F0D' H'0123' H'5E2D1AB4'
Strings define scalar character string data values. The three types of string constants are character form, hexadecimal form, and Hollerith form.
The character form is a delimited string optionally preceded by a C. Apostrophes or double quotation marks may be used for this form. The hexadecimal form is a delimited string of hexadecimal digits preceded by an X. The Hollerith form is a string of bytes preceded by the count of the number of bytes in the string. The syntax is:
< count | string >
The count in the preceding syntax is the number of characters in the string. The QPRCRTPG API ensures that the string contains the right number of characters by checking for the
>
character. No blanks are allowed between
<
and
>
unless they are part of the string. The QPRCRTPG API simply flags the constant as in error if the right corner bracket does not appear in the correct position.
The following groups of strings are equivalent:
'ABCDE' C'ABCDE' X'C1C2C3C4C5' <5|ABCDE> 'TE''ST' "TE'ST" X'E3C57DE2E3' <5|TE'ST> '/*' X'615C' <2|/*>
Packed constants define packed decimal scalar data values. Packed constants are a string of decimal digits delimited with apostrophes. They can have an embedded decimal point and can be preceded by a sign. P must precede the delimited string. Packed constants have a maximum of 31 significant digits.
Note: You must specify at least one numeric digit.
P'+123.456' P'1' P'-1' P'-123.345345345345' P'+.00000000000001'
Zoned constants define zoned decimal scalar data values. The external representation of zoned constants is the same as that for packed constants except that the preceding character is a Z.
Note: You must specify at least one numeric digit.
Z'+123.456' Z'1' Z'-1' Z'-123.345345345345' Z'+.00000000000001'
Floating-point constants define floating-point scalar data values. You must specify whether the constant is a 4-byte (short floating-point) or an 8-byte (long floating-point) value.
There are two ways to represent floating-point values. First, you can specify floating-point constants as a delimited string of decimal digits possibly with an embedded decimal point and optionally preceded by a sign. An F for short floating-point values or an E for long floating-point values must precede the delimited string. An E in the string determines the start of the base 10 exponent. You specify the exponent as signed.
Second, you can specify floating-point constants as a string of hexadecimal digits. The delimited string must be preceded by an XF for short floating-point values or an XE for long floating-point values.
Note: You must specify at least one numeric digit.
Short Floating-Point Long Floating-Point Values Values F'0' E'0' F'+12' E'+12' F'-12.21' E'-12.21' F'12.34E2' E'12.34E2' F'+3.2345678E-02' E'+3.2345678E-02' XF'449A4000' XE'46CE6F37FFBE8722' XF'40490FD0' XE'400921F9F01B866E'
Several special values are allowed:
Short Floating-Point Long Floating-Point Values Values F'MNAN' E'MNAN' Masked Not A Number F'UNAN' E'UNAN' Unmasked Not A Number F'+INF' E'+INF' Plus Infinity F'-INF' E'-INF' Minus Infinity
Note: You must use floating-point constants to initialize floating-point data objects.
Names specified in the intermediate representation of a program are a sequence of characters of up to 48 characters in length. You cannot use the following characters as the first character of the name:
blank /,;():<+'%-0123456789
You cannot use the following characters in subsequent characters of the name:
blank /,;():<+'%
.NAME NAME THIS_IS_A_NAME THIS_IS_A_NAME_2 &NAME !NAME ?NAME .0001
Note: Symbols that begin with a period (.) are not inserted into the program's symbol table and may not be referred to by the i5/OS debug function.
Comments, in the intermediate representation of a program, may appear anywhere in the text. Comments are treated as blanks so they are significant in finding tokens. Comments are a string of characters starting with
/*
and ending with
*/
. If a comment occurs immediately following a semicolon, it prints as a
separate line (or a multiple line as required) on the listing. If a comment is
embedded in a statement, then it appears as a part of that statement, such as a
remark.
The following statements are equivalent:
CPYBLA A,B; CPYBLA A, /* C-> */ B ; CPYBLA A,B; /* B is based on C */
You can use strings of blanks of any length in the intermediate representation of a program. Blanks act as delimiters in finding tokens and in some places are necessary as in separating the opcode and operand in an instruction statement.
The following statements are equivalent:
ADDN A,B,C; ADDN A , B , C ;
| Top | Program and CL Command APIs | APIs by category |