This topic describes how the intrusion detection system works.
Intrusion detection uses the idspolicy.conf file that contains a set of policies for intrusion events. Each policy has an associated condition and action, but there might be more than one condition associated with the same action. The TCP/IP stack reports the most common potential intrusion events and audits them, so that you can write an application to analyze the data and report to the security administrator if intrusions are likely to be underway. The following diagram shows how the intrusion detection function works.
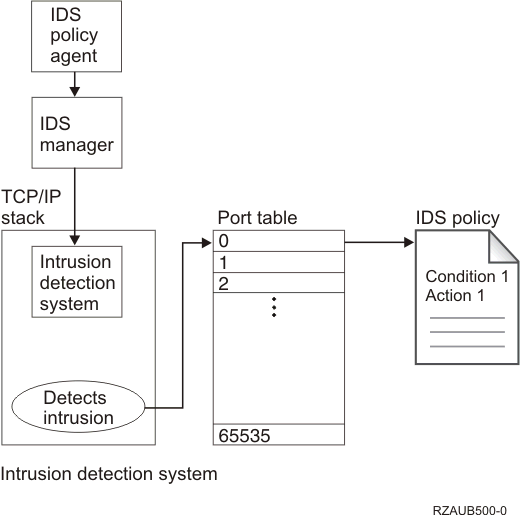
- You edit the idspolicy.conf file to detect specific types of intrusions, and then you start the QoS server.
- The QoS policy agent reads the intrusion detection policy in the idspolicy.conf file.
- The QoS policy agent sends a message with machine instructions to the QoS manager.
- The QoS manager interprets the machine instructions and sends them to the intrusion detection system inside the TCP/IP stack. The TCP/IP stack manages outbound traffic and inbound traffic in the network, and routes requests to other computers in the network.
- The intrusion detection system creates the policies in the port table. The port table entries represent ports 0 through port 65 535. For example, port 0, which contains conditions that apply to all ports, points to intrusion condition 1 which points to action 1. Similarly, port 1 points to condition 2 which points to action 2. Port 1 also points to condition 3 which points to action 1, and so on.
- When the TCP/IP stack detects an intrusion, it looks for matching conditions in the port table and executes the specific action, for example, creating an IM auditing record or system statistics.
- The system creates an IM audit record which describes the type of intrusion event.
- The system administrator analyzes the IM audit record to determine which security actions to take, such as closing off the port from where the intrusion originated.