Use the following scenario to become familiar with the prerequisites and objectives of setting up cross realm trust on your network.
Situation
You are a security administrator for a large wholesale company. Currently you manage security for systems used by employees of the Order Receiving Department and the Shipping Department. You have configured a Kerberos server for the Order Receiving Department. You have configured network authentication service on the iSeries™ system in that department to point to that Kerberos server. The Shipping Department consists of an iSeries system that has a Kerberos server configured in i5/OS™ PASE. You have also configured network authentication service on this iSeries system to point to the Kerberos server in i5/OS PASE.
Since users in both realms need to use services stored on iSeries systems located in each department, you want both of the Kerberos servers in each department to authenticate users regardless of which Kerberos realm they are located in.
Objectives
In this scenario, MyCo, Inc. wants to establish a trust relationship between two already existing Kerberos realms. One realm consists of a Windows® 2000 server acting as the Kerberos server for the Order Receiving Department. This server authenticates users within that department to services located on an iSeries server. The other realm consists of a Kerberos server configured in i5/OS PASE on one iSeries, which provides services for the users within the Shipping Department. Your users need to be authenticated to services in both departments.
- To give clients and hosts on each network access to the other's network
- To simplify authentication across networks
- To allow ticket delegation for users and services in both networks
Details
Detailed description of the environment that this scenario describes, including a figure that shows the topology and all major elements of that environment and how they relate to each other.
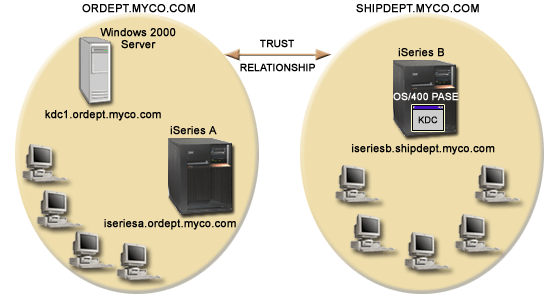
Order Receiving Department
iSeries A
 Runs i5/OS Version 5 Release 3 (V5R3) or later with the
following options and licensed products installed:
Runs i5/OS Version 5 Release 3 (V5R3) or later with the
following options and licensed products installed:
- i5/OS Host Servers (5722-SS1 Option 12)
- iSeries Access for Windows (5722-XE1)
 Network Authentication Enablement (5722-NAE) if you are using
V5R4 or later
Network Authentication Enablement (5722-NAE) if you are using
V5R4 or later
 Cryptographic Access Provider (5722-AC3) if you are running
V5R3
Cryptographic Access Provider (5722-AC3) if you are running
V5R3
- Has network authentication service configured to participate in the realm ORDEPT.MYCO.COM. The i5/OS principal, krbsrv400/iseriesa.ordept.myco.com@ORDEPT.MYCO.COM, has been added to the Windows 2000 domain.
- iSeries A has the fully qualified host name of iseriesa.ordept.myco.com.
Windows 2000 server
- Acts as the Kerberos server for the realm, ORDEPT.MYCO.COM.
- Has the DNS host name of kdc1.ordept.myco.com.
- Each user within the Order Department has been defined in Microsoft® Active Directory on the Windows 2000 server with a principal name and password.
Client PCs
- Run Windows 2000 operating system.
- PC used to administer network authentication service has the following
products installed:
- iSeries Access for Windows (5722-XE1)
- iSeries Navigator
and the following subcomponents:
- Security
- Network
Shipping Department
iSeries B
 Runs i5/OS Version 5 Release 3 (V5R3) with the following
options and licensed products installed:
Runs i5/OS Version 5 Release 3 (V5R3) with the following
options and licensed products installed:
- i5/OS PASE (5722 SS1 Option 33)
- Cryptographic Access Provider (5722-AC3)
- iSeries Access for Windows (5722-XE1)
- Has a Kerberos server configured in i5/OS PASE with the realm of SHIPDEPT.MYCO.COM.
- Has network authentication service configured to participate in the realm SHIPDEPT.MYCO.COM. The i5/OS principal, krbsrv400/iseriesb.shipdept.myco.com@SHIPDEPT.MYCO.COM, has been added to the i5/OS PASE Kerberos server.
- Both iSeries B and the i5/OS PASE Kerberos server share the fully qualified host name iseriesb.shipdept.myco.com.
- Each user within the Shipping Department has been defined in the i5/OS PASE Kerberos server with a principal name and password.
Client PCs
- Run Windows 2000 operating system.
- PC used to administer network authentication service has the following
products installed:
- iSeries Access for Windows (5722-XE1)
- iSeries Navigator
and the following subcomponents:
- Security
- Network
 The KDC server name, kdc1.myco.com, and the
hostname, iseriesa.myco.com are fictitious names used in this scenario.
The KDC server name, kdc1.myco.com, and the
hostname, iseriesa.myco.com are fictitious names used in this scenario.
Prerequisites and assumptions
In this scenario, the following assumptions have been made to focus on the tasks that involve establishing a trust relationship between two pre-existing Kerberos realms.
- All system requirements, including software and operating system installation,
have been verified.To verify that the required licensed programs have been installed, complete the following:
- In iSeries Navigator, expand .
- Ensure that all the necessary licensed programs are installed.
- All necessary hardware planning and setup have been completed.
- TCP/IP and basic system security have been configured and tested on iSeries A.
- Network authentication service has been configured and tested.
- A single DNS server is used for host name resolution for the network.
Host tables are not used for host name resolution.Note: The use of host tables with Kerberos authentication may result in name resolution errors or other problems. For more detailed information about how host name resolution works with Kerberos authentication, see Host name resolution considerations.
- All system requirements, including software and operating system installation,
have been verified.To verify that the required licensed programs have been installed, complete the following:
- In iSeries Navigator, expand .
- Ensure that all the necessary licensed programs are installed.
- All necessary hardware planning and setup have been completed.
- TCP/IP and basic system security have been configured and tested on your iSeries server.
- Network authentication service has been configured and tested.
- All necessary hardware planning and setup have been completed.
- TCP/IP has been configured and tested on your server.
- Microsoft Active Directory has been configured and tested.
- Each user within the Order Department has been defined in Microsoft Active Directory with a principal name and password.
Configuration steps
To set up a trust relationship between two realms, complete these steps.